WHAT IS A BOTNET ATTACK?
A botnet attack is a cyber-attack by Internet-connected devices controlled by a malicious character.
The botnets themselves are four devices. When cybercriminals create malware on a network to control it as a group, they often launch cyber attacks. Botnet attacks can be used to send spam, steal data, compromise confidential information, promote advertising fraud, or launch a Distributed Denial of Service or DDoS attack.
BOT ATTACKS VS A BOTNET ATTACK
Botnet attacks can be thought of as some sort of common “bot” attack. Bot attack is a cyber attack that uses automated web applications to disrupt a website, application, or device.
The Bot attack initially involved simple spam operations but has turned out to be more complex, intended to defraud or defraud users. One of the reasons for this is the availability of open-source tools for building bots, known as bot kits.
These bot kits, often available for free on the Internet or on the Web, can be used to perform malicious activities such as website scraping, account retrieval, harassment of forms, and botnet attacks, including DDoS attacks.
HOW DOES A BOTNET ATTACK WORK?
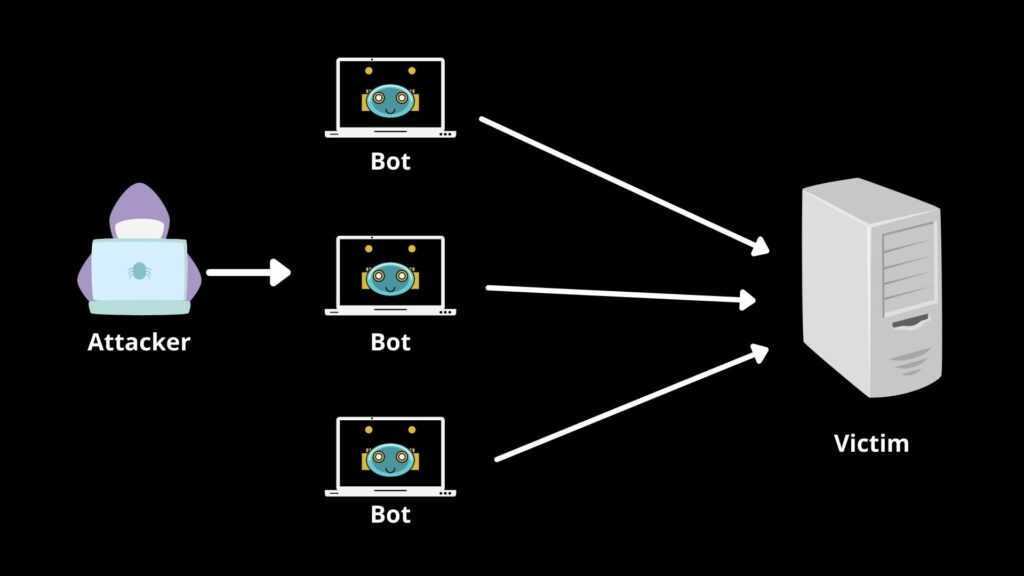
The Botnet attack begins with cyber criminals gaining access to devices by endangering their security. They can do this with hacks like Trojan virus injections or basic social engineering tricks. These devices are then controlled using software that instructs the devices to attack a large scale.
Sometimes, criminals themselves may not use the botnet to launch an attack, but instead, they sell network access to other bad players. These third parties can use the botnet as a “zombie” network for their own needs, such as directing spam campaigns.
DIFFERENT TYPES OF BOTNETS
Botnet attacks may vary depending on their methods and the tools they use. Sometimes these bottles themselves do not attack but become a way for criminals to launch second-party campaigns such as fraud and ransom attacks. Some of the most common types of botnet attacks include:
- Distributed Denial-of-Service (DDoS) Attack: One of the most common types of botnet attacks works by overloading a server with web traffic sent by bots to crash it. This downtime on server performance can be used to launch additional botnet-based attacks.
- Attack of identity theft(phishing attacks): This is often presented to disclose important information to employees of an organization. For example, bulk campaigns can be designed to mimic reliable sources to trick people into disclosing personal data such as login details, financial information, and credit card details.
- Cruel attacks (BruteForce attacks): These include programs that forcefully override web accounts. Dictionary attack and authentication focus are used to exploit weak users’ passwords and access to their data.
WHAT ARE THE MOST DANGEROUS PROGRAMS AND DEVICES?
When a botnet attack makes news, the damage is often referred to as the number of computers or servers compromised. But it is not just individual programs that can be infected and reduced. Any device connected to the Internet is at risk of being attacked by a botnet.
With the growth of IoT, more and more devices are joining the internet, which increases the chances of vector attacks. Even wireless CCTV cameras that look harmless from your balcony or yard may be at risk of opening the botnet malware access point for network access. The fact that new IoT devices can come with unsafe security settings only exacerbates the problem.

DETECTING BOTNET ATTACKS
Botnet attacks are difficult to detect because the user often does not know when the device is in danger. Some botnets are designed with a central server that controls each bot in the control and control model. In these bottles, an important step in detecting an attack involves finding that central server.
Standing analytical techniques can help detect infection in devices. This applies when the device is not using any programs and includes checking for malware signatures and other suspicious communications on control and control servers looking for active commands and suspicious files. As botnet creators develop more strategies to avoid detection, they are getting better at avoiding static analysis methods.
Behavioral or dynamic analysis can also be used when there are many resources available. This includes scanning ports on local networks and looking at unusual Relay Chat (IRC) traffic activity.
Antivirus software can detect botnet attacks to some extent but fail to detect infected devices. Another exciting way is to use honeypots. These are fake programs that catch botnet attacks using a fraudulent login opportunity.
With large botnets, such as Mirai botnet, ISPs sometimes work together to track traffic and figure out how to stop botnet attacks. They can work with security companies to identify other devices that have been compromised on the network.
CAN BOT ATTACKS BE PREVENTED?
Preventing botnet attacks has become more complicated in recent years. One of the biggest challenges in preventing this attack is the proliferation of devices. As different types of devices are readily available, often with their own security settings, it becomes difficult to monitor, track, and stop these attacks before they occur. However, you can still take certain steps to prevent botnet attacks.
- Keep all programs updated.
One of the main ways bottled ups is to enter and compromise a business security system using the risk of uninstalled network equipment. This makes it very important to keep the systems up to date and to ensure that new updates are installed as soon as they become available.
This includes hardware devices, especially legacy devices, that can remain neglected in businesses when they are no longer actively used.
- Develop the best internet security
This includes hardware devices, especially legacy devices, that can remain neglected in businesses when they are no longer actively used.
- Embrace the best cyber security measures
It is important to follow basic security hygiene on all devices in order to maintain botnet attacks. This includes using complex passwords, educating employees about the dangers of email theft to steal sensitive information, and clicking on suspicious attachments and links. Businesses should also take appropriate steps to ensure that any new device that enters their network has sound security settings.
- Control access to machines
Taking steps to lock access to machines is another way to prevent botnet attacks. In addition to strong passwords, you should also use multi-factor authentication and access control only for those who need it most. Suppose access to sensitive systems is controlled and isolated from each other. In that case, it is a little easier to detect botnet attacks on a specific set of devices and end them there.
- Monitor network traffic using mathematical solutions
Preventing botnet attacks requires good tactics to get you ahead of time. Using advanced analytics to monitor and manage traffic flow, user access, and data leaks are other steps you can take. Mirai botnet is one of the situations where attackers have used unsecured connected devices.

HOW TO MITIGATE AGAINST BOT ATTACKS
Sometimes even your best security measures can be compromised by a botnet attack, and it’s too late when you find yourself on your network. In such cases, your best bet is to minimize the impact of the attack. This means reducing the damage that will be caused.
- Disable central server
Botnets designed for the control and control model can be disabled when a central service or server is available. Think of it as determining a brain surgeon to take over the entire botnet.
- Run antivirus or reset the device
For vulnerable computers, the goal should be to regain control. And this can be done by using antivirus software, installing software, or restarting the system from scratch. In the case of IoT devices, you will need to turn on the firmware, complete a factory reset to minimize botnet attacks.




