What is a cryptocurrency?
A cryptocurrency is a digital currency system with two main variations that distinguish it from traditional currencies. First, cryptocurrency is not tied to or sponsored by any government, making it a truly international currency. Second, cryptocurrency is constantly being distributed.
What is blockchain?
A blockchain is a digital, public book that records online transactions. Blockchain is a key technology for cryptocurrencies such as bitcoin. The blockchain guarantees the integrity of the cryptocurrency by encrypting, verifying, and permanently recording the transaction. The blockchain is similar to a bank ledger but open and accessible to anyone who uses cryptocurrency is supported.
What is cryptocurrency mining?
Cryptocurrency mining, or crypto mining, is a process in which transactions for various digital currencies are verified and deposited in a digital blockchain ledger. Also known as crypto coin, altcoin mining, or Bitcoin mining (the most popular form of digital currency, Bitcoin), digital currency mining has risen as a topic of profit and activity as the use of cryptocurrency itself has grown significantly over the past decade.
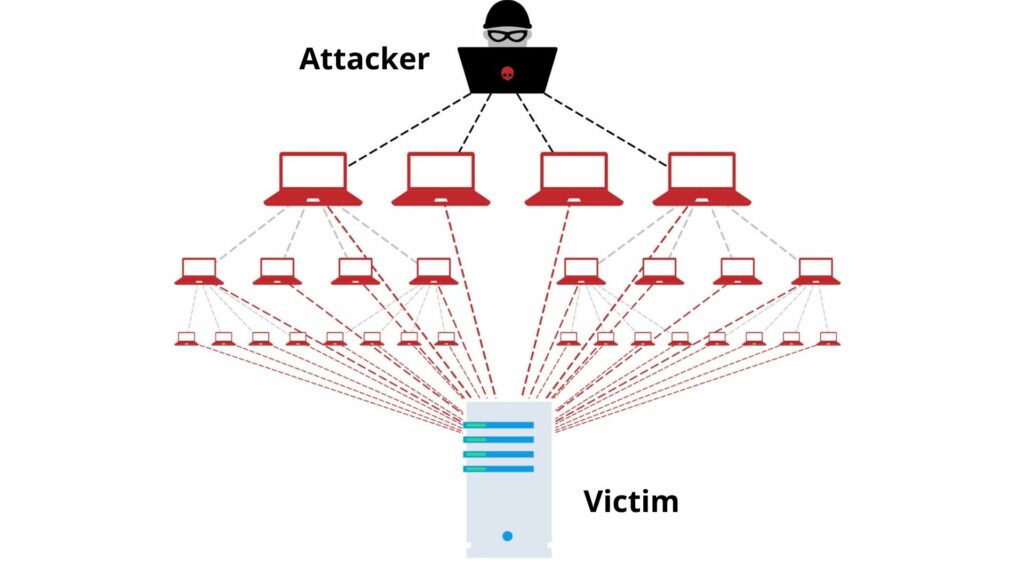
Why are cryptocurrencies being DDoSed?
Like many apparent businesses, currency exchanges have been targeted at DDoS attacks. With the rise in interest and a further increase in traffic around cryptocurrencies, the door has been opened for bad characters to try to disrupt cryptocurrency resources.
Distributed Denial of Service (DDoS) is one of the primary sources of disruption in today’s Internet. By overloading a target with fake traffic, a bad character can make a website or service unavailable. The popularity and importance of cryptocurrencies make them a critical factor in the attack.
We have been analyzing some of the DDoS attacks hitting many financial transactions on our network to measure any apparent patterns of interest. The most significant DDoS traffic came from SSDP enhancement attacks, NTP expansion attacks, and application-layer attacks.
One popular currency exchange service has been flagged with an attack on 76 applications for a year; however, it is essential that surprising traffic awareness can create false positives where regular traffic can show some signs of attack. No matter, it is clear that bitcoin exchanges have been the main objectives of DDoS.
Here is a graph showing the number of application-layer attacks that may point to popular cryptocurrency websites in mid-December 2017.
Cryptocurrency DDoS Attack Frequency
Most interestingly, there was a massive spike in the attacks around November 11. At this point, several blockchain fundraising sites seem to be targeted. Fortunately, our DDoS mitigation software and infrastructure have been able to prevent service interruptions.
Even in extreme cases, many websites and apps related to bitcoin and other cryptocurrencies do not have the resources to deal with the massive increase in traffic. Such an increase may occur during a DDoS attack or high normal activity levels, resulting in temporary expiration and denial of service. CDN hosting content may be necessary for keeping the site online, or it may take a modified network of servers to handle the number of database requests that may be displayed.




