What is DDoS blackhole routing?
DDoS is a blackhole routing or blackholing counter agent to reduce DDoS attacks that direct unwanted network overload in the so-called “blackhole” and lost. But why use the blackhole route? Unnecessary traffic flooding network streams and equipment from various transmission museums, deliberately produced by a denial of work denial.
The primary purpose of DDoS attacks is to eliminate access to resources such as bandwidth, CPU, RAM, and other remote devices so that the service is not limited to legitimate users. Users may experience excessive bandwidth usage, or the CPUs may be exceeded by some of the common symptoms associated with this attack. This creates the need to discard DDoS traffic targeted at the black hole as a countermeasure to prevent this type of attack. The blackhole internet route is based on the IP address of the source and location, where the most commonly used process is remote filtering, using the destination IP.
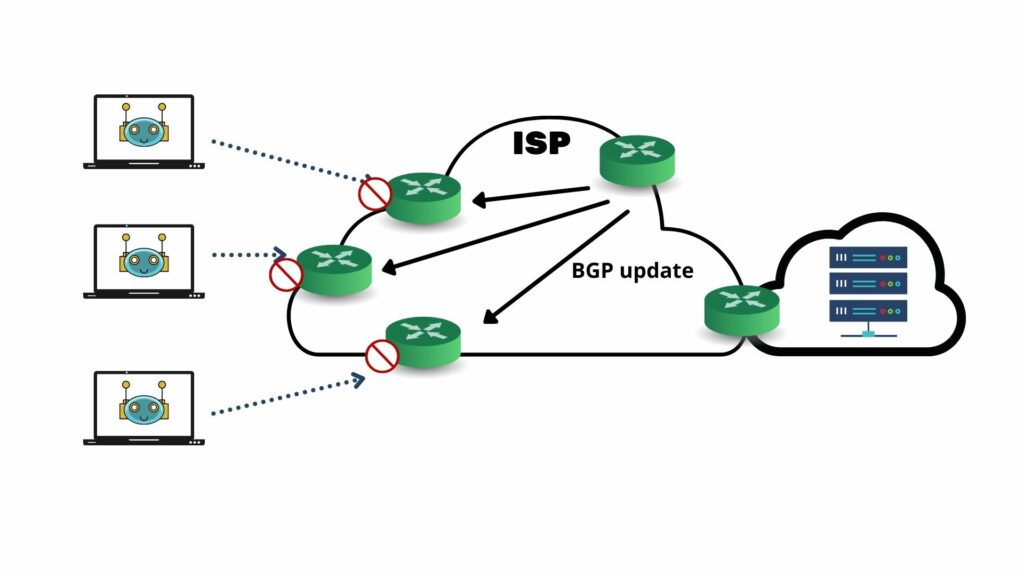
How does blackhole routing work?
DDoS traffic should be diverted and dumped near the source of the attack. The Blackhole Route involves using both local and local IP addresses and, as mentioned above, is the most widely used process, using remote route filtering. For example, a DDoS attack starts on a web server with an IP address 172.12.0.2.
When a customer asks the ISP to filter the current DDoS, it creates a fixed path to the target IP address 172.12.0.1/32, pointing to the null interface. The static channel is distributed during IBGP times from the trigger mechanism to the PE route but with the updated hop IP address to 192.0.2.1. As a result, the total network traffic is redirected to this IP address, thus reducing the void route to PE routers. When the DDoS attack is complete, the static router 172.12.0.2 is removed from the created machine and withdrawn from the IBGP system.
How can blackhole routing help you?
Undoubtedly, you can direct all unwanted traffic into a black hole to end it with a black hole where there is no return.YouTube break for hours was because the ISP sent all the network routes to a useless route and then accidentally shared an invalid network route to other ISPs via IBGP (internet Broadway Gateway Protocol); YouTube’s entire street is littered with garbage dumps around the world.
Walking on a black road can help get rid of all the dangerous roads in the event of an attack, for example, DDoS or a caterpillar attack where a black hole route is seen as an excellent solution to reduce leisure time. In addition, unlike ACL (Access Control List), you can use another solution because the traffic flow works in a Cisco router forwarding method. You can use a black hole router to immerse the same traffic with the benefit of reducing the impact performance on the cisco router itself.
Why use a blackhole route as the cost calls for ACL mainly because ACL requires high processing power in the cisco IOS order of operation? ACL will work in the same way as a black road lead but may require other features to do so.




