What is the High Orbit Ion Cannon (HOIC)?
High Orbit Ion Cannon (HOIC) is a popular tool used to launch DoS and DDoS attacks, which aims to flood the victim’s network with web traffic and shut down a website or service. It is an easily accessible piece of open-source software developed by an anonymous hacktivist group. It follows an old DDoS tool called Low Orbit Ion Cannon (both named after sci-fi video game weapons). While many malicious software tools require a high level of technical expertise, HOIC provides a simple and easy-to-use interface that will be open with the click of a button.
Although used in many dangerous and illegal attacks, HOIC is still officially available because it has applications as a valid testing tool for users who want to use “pressure testing” on their networks.
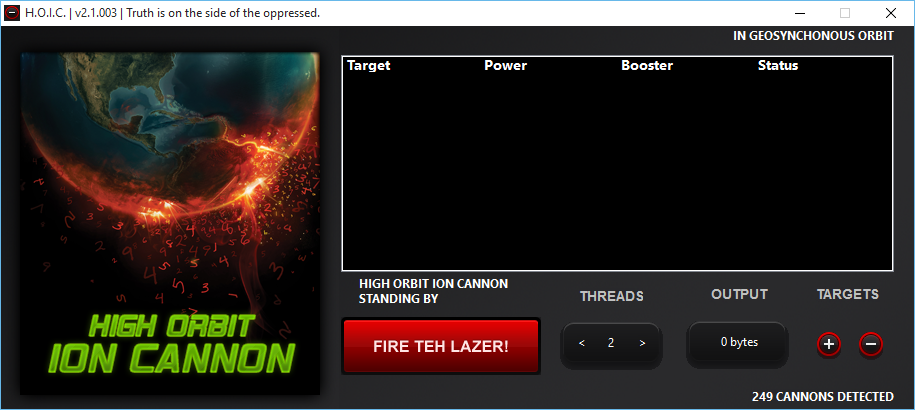
How does the HOIC work?
HOIC is working on the HTTP Flood DDoS application layer attack, flooding the victim’s server with HTTP ‘GET’ and ‘POST’ requests to overload the server request volume. With advanced attacks, custom textswill used to target multiple domains of a victim’s site at once. HOIC can also target as many as 256 sites simultaneously, making it easier for users to interact with the attack simultaneously. This ‘gun method’ of having multiple attackers targeting multiple pages and domains simultaneously can make mitigation and recovery efforts a major challenge.
Built-in booster scripts also help attackers avoid detection. In addition to supporting documents, many HOIC users use Swedish proxies to specify their location (They prefer Sweden because of strict online privacy laws in that country).
Launching a critical attack with HOIC requires some integration, as it requires about 50 different users to start the same target attack simultaneously. Anonymous showed off the HOIC operation in 2012 when it successfully launched an attack on major record companies, the RIAA, and the FBI. It was one of the largest DDoS attacks in history and required an estimated 27,000 computers simultaneously using HOIC.
How to protect against HOIC?
There are several strategies to reduce HTTP flood attacks from HOIC. IP Address Filter (IPRF) is a blockchain method that detects incoming IP addresses against infringing IP address information and keeps traffic out of the network. Web Application Firewall (WAF) may set rules to limit traffic levels from IP addresses that create suspicious applications. There are also ways to test whether a web client is legitimate, such as captcha verification and a more sophisticated method that asks web browsers to solve a simple math problem without interfering with user information.




