DDoS mitigation answers are do not prepare for surprising attacks; they come to be aware of and get over DDoS attacks after a hit. Many corporations depend on their DDoS protection at the arms of DDoS mitigation companies that provide DDoS mitigation solutions. Still, these robust DDoS answers haven’t any way of detecting DDoS vulnerabilities earlier than a network is attacked. They act after the assault and go into the “tight” to lessen the attack – this means that the companies are crushed, dropped, but later recover. Relying on the mitigation abilities, signatures of SLAs, and durability is determined, how long it takes for offerings to be restored. This number may be everywhere in 30 seconds, up to three days.
The shortcomings in mitigation solutions are glaring and can be seen in DDoS assaults that keep motiving extreme harm to groups worldwide. In May 2021, a first-rate DDoS attack became why many Belgian net components have been declining. Numerous companies in Belgium, including the authorities and parliament, were affected by the DDoS assaults, leaving them with an awful tune record.
Remaining 12 months, Amazon internet services (AWS) changed into a hit by an effective assault. This 2.3 terabit assault, in keeping with 2nd, lasted more than three full days. There were numerous DDoS attacks in September 2021, and we were capable of creating an outline file. All in any other case, a maximum of the affected organizations have mitigation solutions. Large assaults maintain to occur to capture companies, businesses, governments, and every so often all offline countries. for plenty such groups, disruption of statistics era (IT) services may be directly associated with misplaced sales. Here’s a listing of the top four industries suffering from DDoS attacks. Ultimately, consumer expectations have risen, and there are expectancies for normal-existing connections, which means organizations cannot have enough money for entertainment time.
The Evolution of DDoS Attacks
The upward thrust of the internet of things (IoT) has changed the gambling discipline concerning DDoS attacks. IoT devices typically have less security, making them the great equipment you may use to produce duplicate traffic. Hackers begin hijacking huge numbers of IoT devices and use them to create massive botnets. With such botnets, the amount of visitors the attacker can ship to a target jumps from gigabytes to terabytes.
The whole improvement of networks and server infrastructure additionally accidentally makes DDoS assaults extra powerful. The introduction of networks including 5G gives many benefits to customers and presents a great way to create tremendous DDoS floods. Because 5G offers excessive bandwidth and low latency, hackers can now create big IoT botnets that might be sufficient to threaten internet hackers like Google or Amazon.
Critical Reasons To Hurt DDoS Attacks Despite Reduction Solutions
- Mitigation solutions are robust but need to be considered and continually improved. However, it is not possible in today’s climate because network vulnerability often changes as new services and applications are added. As a result, expired configurations leave systems open to new DDoS vulnerabilities.
- DDoS attackers are cunning, here have been several attacks over the years that are low and slow, i.e., attacks are focused on loading the service, but it does not impose limitations of the mitigation system, creates a set of different attacks that combine to slow down services, take longer to find, and cause
- DDoS attackers also initiate multi-vector attacks using complex combinations of different attacking vectors for other purposes, making it more difficult for mitigation systems and services to focus on what is happening and what should be prevented first. This strategy effectively achieves long periods of rest before the onset of attacks and mitigation. Here’s an attractive fact sheet on how Hackers continue to learn DDoS security limitations and launch multiple vector attacks.
- Long-term mitigation is based on the realization that, in many cases, DDoS security systems have the low response time required to detect malicious DDoS traffic and that reducing attacks requires more time. Hackers exploit this problem by changing the attack strategies (vectors and target combinations) in a shorter time than the response time of the defense system to avoid triggering the mitigation system. A series of such fast attacks would cause damage to the targeted network services.
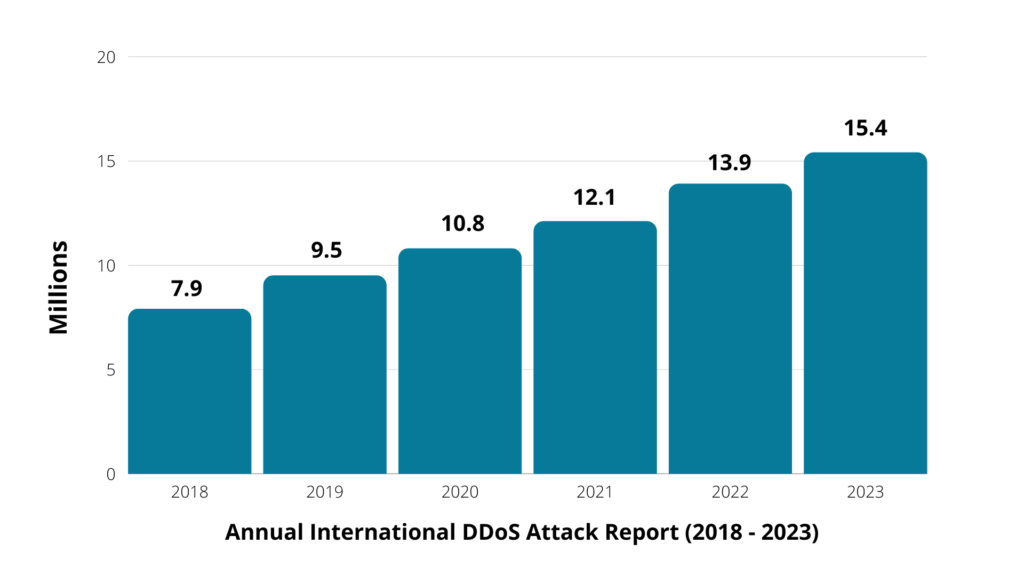
Number of DDoS Attacks will be double to 15.4 million by 2023 globally:
So, is it possible to prevent this attack? Is there a more efficient and intelligent way to stay afloat than a DDoS attack?
Mitigation solutions can’t save you or forestall all DDoS attacks without continuous suspension. They had been able to pick out the stopping and mitigation gaps after the attack had already lowered the community. Enterprise options may be decided by whether they need to be crucial to decreasing assaults or whether or not they want to ensure that community vulnerabilities are identified and closed down constantly.
What will be the Future of DDoS Attack?
Modern-day practice shows that DDoS assaults will be more significant, not unusual, intense, and powerful. The proliferation of IoT devices and the speedy implementation of 5G capabilities global will be a deadly aggregate. Similarly, continuous commercial enterprise pricing has taken a toll on the COVID-19 epidemic. As a result, organizations of all sizes have a good component in their online property, making them appropriate gemstones.
With regards to defensive DDoS, the current situation is some distance from perfect. Hackers have efficaciously used cloud generation to create DDoS. businesses want to conform speedily and begin enforcing similar answers in their safety cells. However, hackers usually seem to be one step beforehand regarding strategies, techniques, and methods.
Inside the first half of 2020, there had been greater than 4.83 million DDoS assaults. This determination has risen sharply from the stressful numbers of 2019. We can only anticipate this trend to preserve in 2021 and beyond.




