What is an NTP expansion attack?
NTP attack to increase power-based attacks (DDoS). The attacker uses the Network Time Protocol (NTP) server to terminate a network or server targeted with increased UDP traffic, making the target and surrounding infrastructure inaccessible to regular traffic.
How does an NTP augmentation attack work?
All scalability attacks exploit bandwidth cost inequalities between attackers and targeted web resources. When cost differences are magnified in all multiple applications, the resulting traffic volume can disrupt network infrastructure. A malicious user can get more out of the small by sending small questions that lead to great responses. When you replicate this magnification by making each bot in the bottle make the exact requests, the attacker is both caught up in reaping and reaping the benefits of the most widespread attack traffic.
DNS flood attacks are different from expansion DNS attacks. Unlike DNS floods, DNS boost attacks show and increase traffic to unprotected DNS servers to hide the attack’s origin and increase its effectiveness. DNS Amplification attacks use devices with low bandwidth connections to make multiple requests to unprotected DNS servers. Devices make many small requests for extensive DNS records, but the attacker makes the return address the victims when they make requests. Enlargement allows the attacker to capture larger targets with limited attack resources.
Expanding NTP, like growing DNS, can be thought of in the context of a dangerous teenager calling the restaurant, “I’ll have it all, please call me and tell me my whole order.” When a restaurant asks for a callback number, the given number is the target phone number. Targeted and received a call from a restaurant with a lot of details they didn’t ask for.
Network Time Protocol allows Internet-connected devices to synchronize their internal clocks and play an essential role in constructing online structures. By using the monlist command enabled on other NTP servers, the attacker can duplicate the traffic of his first request, which results in a tremendous response. This command is automatically enabled for older devices and responds with the last 600 IP addresses of requests made to the NTP server. A monlist request from a server with 600 addresses in its memory will be 206 times larger than the original application. This means that an attacker with 1 GB of internet traffic can bring in 200+ gigabyte attacks – a huge increase in emerging attack traffic.
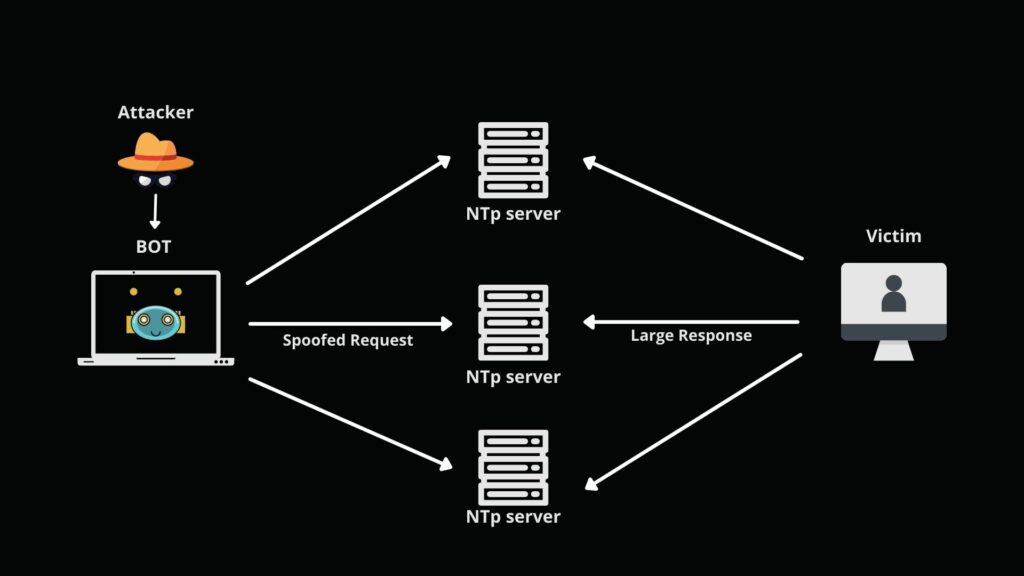
An NTP amplification attack can be broken down into four steps
- The attacker uses a botnet to send UDP packets with fake IP addresses to an NTP server with its listing command enabled. The fake IP address in each package points to the actual IP address of the victim.
- Each UDP packet requests an NTP server using its listing command, resulting in a larger response.
- The server then responds to the corrupted address with paid information.
- The target IP address receives a response, and the surrounding network infrastructure is disrupted by traffic, which has led to a denial of service.
How is a NTP amplification attack mitigated?
For a person or company running a website or service, mitigation options are limited. This stems from the fact that although it may be the target, the individual server is not where the greatest impact of volumetric attacks is found. Due to the high number of roads created, the infrastructure around the server is feeling the impact. Internet Service Provider (ISP) or other emerging infrastructure providers may not manage incoming traffic without interruption. As a result, the ISP may block all traffic to the target IP address, protect itself and remove the target site off-line. Mitigation strategies and illegal security services such as Cloudflare DDoS protection, particularly Internet infrastructure security solutions.
With a well-designed firewall and sufficient network capacity, it is small to block an attack that shows up as an NTP attack to increase power. While the attack will target a single IP address, our Anycast network will spread all the attack routes until it no longer interferes. During the last six-month window, our DDoS mitigation program “Gatebot” received a simple attack of 6 329 (that alone every 40 minutes), and the network successfully minimized everything.




