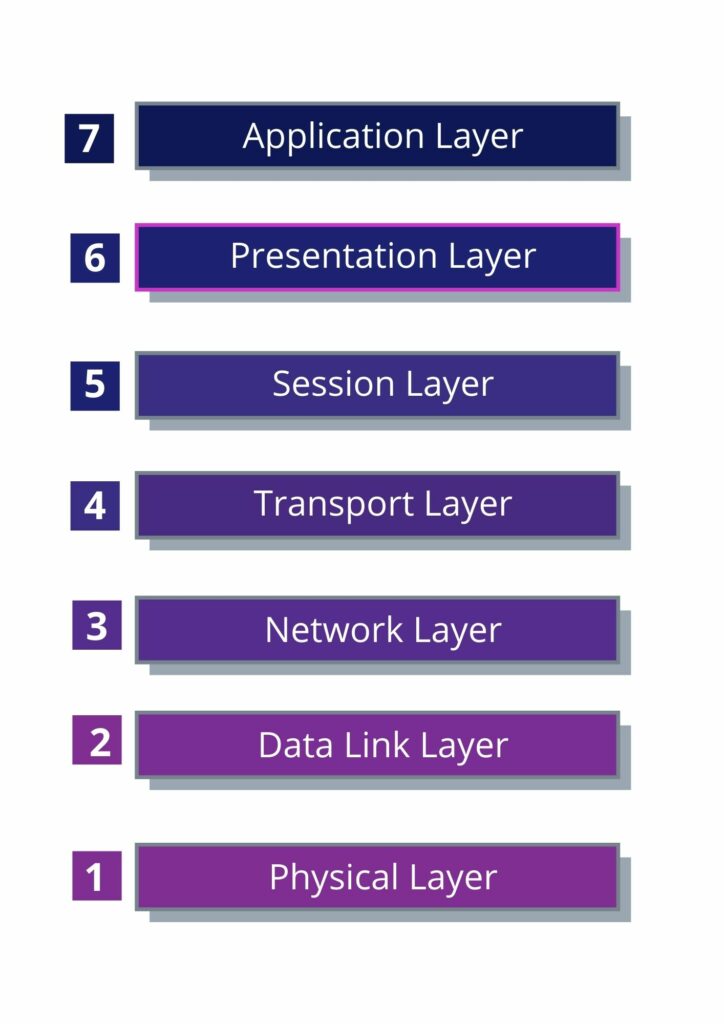
The OSI reference model consists of seven different layers and is the first standard model of network communication. It’s implemented by all primary computer and telecommunications companies
OSI is a conceptual model developed by the International Organization for Standardization that enables various communication methods to communicate using standard protocols. Although not comprehensive, the simple TCP/IP model is still in use today and allowed for greater connectivity among users. While the OSI 7-layer model is still widely used for communicating how networks operate, it also solves communication issues. Adding to this, it helps visualize how they work.
The history of OSI date back to 1983 with the involvement of organizations representing various important IT companies. It was also recognized by ISO as a global standard in 1984.
The 7 Layers of the OSI Model:
7. Application layer
The application layer is used by end-user software such as web browsers and email clients. It provides protocols that allow software to send and receive information. Software applications such as web browsers and email clients depend on the app’s layout to initiate communication. The application layer is used by end-user software like web browsers and email clients. It provides the protocols that help your apps send and receive information more easily. Apps like web browsers and email depend on the application layer to get their work done faster. However, it should be noted that client software apps aren’t part of the application layer – instead, the application layer deals with things like contracts and data fraud. The software relies on this to deliver meaningful data to the user. HTTP, FTP, and POP are all examples of Application Layer protocols. They work by sending data packets between computers on a network. Common protocols include SMTP and DNS which help your computer find the destination computer so that your message can be delivered.
6. Presentation Layer
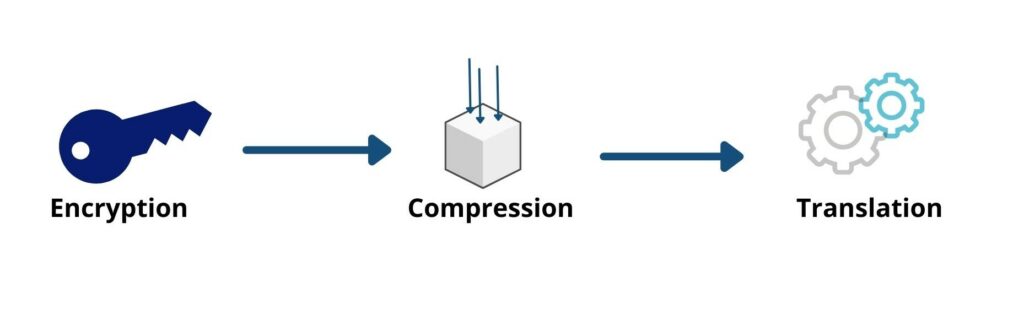
If data passes through the Application Layer it must be encrypted, compressed and then re-encrypted at the Presentation Layer. This keeps your content safe to use on any device. The presentation layer is responsible for making information easier to read. It takes data, prepares it and transfers it to the session layer. When two devices are in communication, they may choose to use different methods of encoding. As a result, layer 6 translates the incoming data into syntax that is delivered by the device’s application
When a device communicates securely with another through encryption, layer six adds the end to end encryption right before it reaches the application layer. This helps keep the final message readable.
5. Session Layer
A Session Layer creates connections (Sessions) between devices. This layer is responsible for opening and closing connections and the time spent in a connection is known as a session. The session layer’s code allows for the transmission of all changing information and closes when no more data is produced. This’ll keep your sessions open just enough to transmit all transmitting data and close when no more transmissions are necessary.
The session layer also synchronizes data transfer with testing locations. This way, if you are transferring a 100-megabyte file, for example, the session layer can set up a viewing point every 5 megabytes. For instance, if someone has disconnected before the transfer is completed or the computer crashes after having transferred 52 megabytes of data, then that person will still be able the session may be restarted from the final test location, meaning that there are only 50 megabytes of data to transfer. Except for the viewing areas, all data transfers will have to start over again.
4. Transport Layer
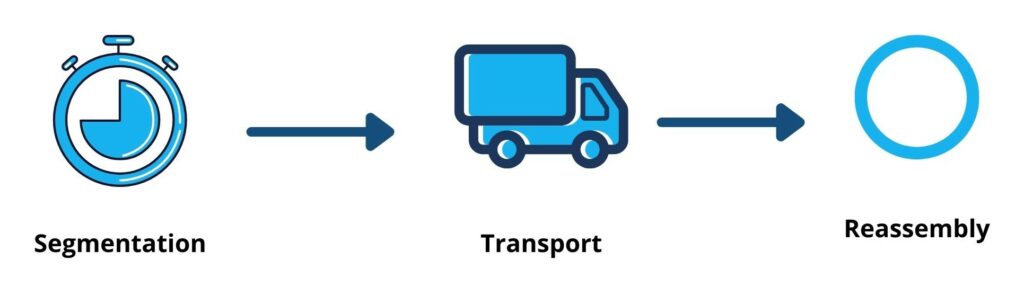
The transport layer handles data transferred in the session layer. As a result, it divides each packet of data into segments before sending them to the receiving end. On top of that, Layer 4 deals with communication between two devices at the end-to-end level. This process involves taking data from a client’s session layer and sorting it into different sections called layers before transferring it to the user’s device. The transport layer on the acquired device is responsible for merging these components into its data layer.
The transport layer controls the flow of data to ensure that it’s sent at a rate appropriate for the transmission speed. It also manages error management. Once the data has been received, the transport layer checks it for completeness and requests a resend if necessary.
3. Network Layer
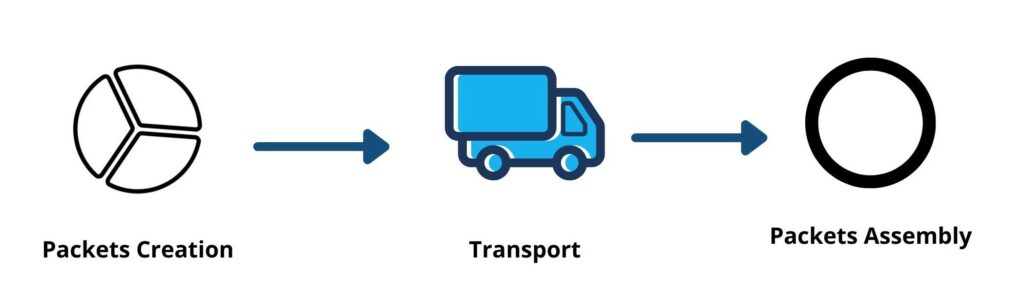
Network Layers have two main functions: One is to package data into network packets and the other is to help in sending packets from a Network Layers have two main functions: One is to package data into network packets and the other is to help in sending packets from a sender’s machine to a receiver’s machine over different networks. If you don’t have a network layer in place, you will not need an intermediary to process the data. This intermediary separates all of the different parts of your network into smaller fragments called packets. It sends these packets to your computer and reassembles them when they arrive. The network layer finds a new, efficient way for data to reach its destination. This is done by looking for a route.
2. Data Link Layer
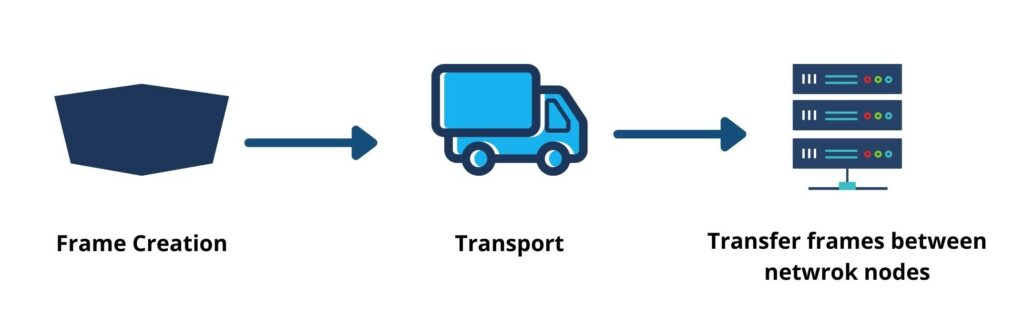
The data link layer works to establish & terminate a connection between two physically connected devices. It is very similar to the network layer, except for the ability it has to send data between two tapped devices. Data link layer is what separates packets into frames, splitting them up for the network layer. The data link layer also controls data flow and checks for errors.(The transport layer controls the flow of data, but does not handle any errors. Communication happens only within the network.)
1. Physical Layer
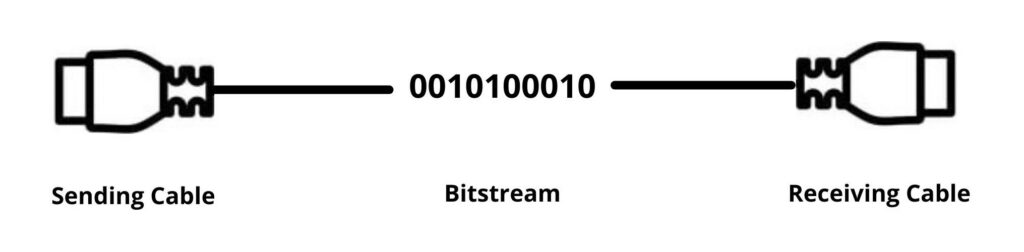
The physical layer is responsible for the physical connection between the network nodes. It includes components like cables and switches that connect and transmit all of the data. They convert any data into a format that can be transferred over the medium (like cables).The two layers of both devices also agree on the signal assembly, with 0s separating the 1s on both devices.
Security in the body layer is easily threatened by unauthorized access or environmental factors such as power grid malfunctions. Cyberattacks on critical infrastructures can end in a Denial-of-Service attack preventing access to important apps and the internet. With biometric verification, electromagnetic protection and advanced locking methods, IT security has become much more robust to ensure safety.