What is OWASP?
Open Web Application Security Project (OWASP) is a non-profit foundation dedicated to improving software security. OWASP operates under the ‘open community model, where anyone can participate and contribute to projects, events, online discussions, and more. OWASP’s guiding principle is that all materials and information are freely available and accessible on their website to everyone. OWASP provides everything from tools, videos, forums, projects to events. In short, OWASP is a repository for all web application security, backed by the in-depth knowledge and experience of its open community providers.
What is the OWASP Top 10?
OWASP maintains a top 10 list and has done so since 2003. Every 2-3 years, the list is updated according to the developments and changes in the AppSec market. The importance of OWASP lies in the practical information it provides; it serves as a key checklist and level of Web application development for many major international organizations.
What are the latest OWASP Top 10 categories?
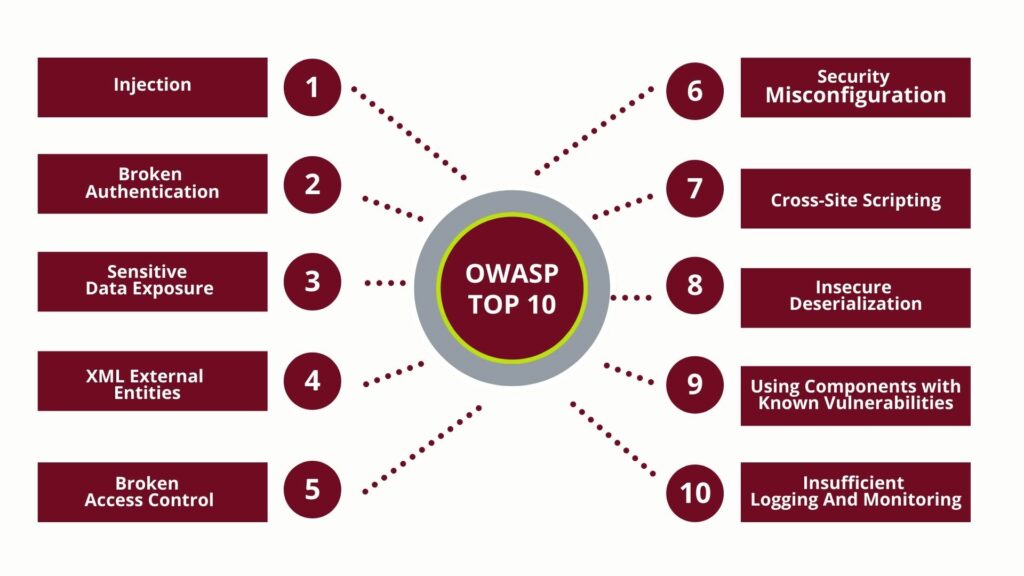
1. Injection
The code injection occurs when an attacker sends invalid data to a web application. The attacker’s purpose is to make the app do something that it was not designed to do.
- Example: SQL injection is one of the most common injection errors found in applications. SQL injection errors can be caused by unreliable data usage by the application when creating an endangered SQL call.
- Solution: Updating source code is the best way to prevent injection attacks. Installing SAST and DAST tools in your CI / CD pipeline helps identify errors for recently introduced injections. This allows you to self-identify and minimize pre-production production.
2. Broken Authentication
Specific programs are often misused. Specifically, operations related to authentication and session management, if misused, allow attackers to loosen passwords, keywords, and times. This can lead to stolen user identity and more.
- Example: A web application allows the use of weak or known passwords (e.g., “Password1”).
- Solution: Multi-factor authentication can help reduce the risk of compromised accounts. Automatic static analysis is very helpful in detecting such errors, while manual static analysis can add strength to testing custom verification schemes. Synopsys ’Coverity SAST solution includes a tester specifically identifying the risk of broken validation.
3. Sensitive Data Exposure
Disclosure of sensitive data is when stored, or transmitted data (such as social security numbers) is compromised.
- Example: Financial institutions that fail to adequately protect their sensitive data can be easy victims of credit card fraud and data theft.
- Solution: SAST tools such as Coverity and SCA tools such as Black Duck Binary Analysis include features and indicators that identify security risks that could lead to the disclosure of sensitive data.
4. XML External Entities (XXE)
Attackers can take advantage of web applications that process XML’s endangered components. Attackers can upload XML or insert hostile commands or content within an XML document.
- Example: An application allows unreliable sources to perform XML uploads.
- Solution: The Static (SAST) application security test is very helpful in locating XXE in the source code. SAST helps test both app configuration and dependency.
5. Broken Access Control
Broken access control is when the attacker can gain access to user accounts. The attacker can act as a user or administrator in the system.
- Example: An application allows a pivotal key to be changed. When a key is transferred to another user’s record, that user’s account can be viewed or changed.
- Solution: It is important to use login testing to detect unintended access controls. Changes in design and design can be ensured to create confidence limits for data access.
6. Security Misconfiguration
Improper security adjustment is when a design or configuration weakness arises from a configuration error or failure.
- Example: The default account and its original password are still active, making the system vulnerable to exploitation.
- Solution: Solutions such as Synopsys ’Coverity SAST include a tester that identifies the disclosure of information found in the error message.
7. Cross-Site Scripting (XSS)
XSS attacks occur when an application inserts unreliable data into a web page. Attackers put separate customer credentials on this webpage.
- Example: Unruly data in an application allows the attacker to ‘steal a user session’ and access the system.
- Solution: SAST solutions well-versed in data analysis can be a great tool to help detect these critical errors and suggest solutions. The OWASP website also provides a cheat sheet for best practices to eliminate such defects from your code. With OWASP’s top categories, such as XSS, which also have a Common Weakness Enumerator (CWE), Black Duck will inform teams that these vulnerabilities lead to vulnerability, enabling them to better understand risk and prioritize their corrective efforts.
8. Insecure Deserialization
Unprotected defamation is a risk when deserialization errors allow the attacker to remotely encrypt the program.
- Example: An application is at risk because it mitigates the hostile content provided by the attacker.
- Solution: Application security tools that help detect deserialization errors and login tests can be used to verify the problem
9. Using Components With Known Vulnerabilities
This accident title refers to its nature; describes when programs are built and operated using materials that contain known risks.
- Example: Due to the volume of materials used in construction, the development team may not know or understand the materials used in their program. This can lead to them becoming obsolete and therefore at risk of being attacked.
- Solution: Software analysis tools (SCA) such as Black Duck can be used next to static analysis to identify and detect obsolete and unsafe items in your application.
10. Insufficient Logging And Monitoring
Login and monitoring are tasks that must be performed on a website frequently to ensure that they are secure. Failure to adequately enter and monitor the site leaves us at risk for more critical occupations.
- Example: Experimental events, such as login, failed login, and other important functions, are excluded, resulting in a compromised application.
- Solution: After performing the entry test, engineers can read the test logs to identify potential defects and defects. SAST solutions can also help to identify offline security




