Will Meris DDoS Botnet Attack Ever Rule the World?

What is Meris? The Meris botnet is a type of malware that hijacks computers and networks to send spam, phishing messages, and other types of email. The botnet consists of infected computers that send out a large number of emails. It is one such attack which utilizes everyday devices like webcams and DVR’s to compromise […]
Top 10 popular types of DDoS Attacks

Volumetric attacks Volumetric attacks are more sophisticated than their predecessor, Distributed Denial of Service (DDoS) attacks. They can be used to target an internet connection and cause widespread damage. This makes them hard to anticipate & prevent with traditional tools Volumetric Attacks are a type of DDoS attack that doesn’t attempt to affect any data […]
Forward Proxy vs Reverse Proxy

A reverse proxy server can absolutely be very useful at guarding your company servers from inevitable attacks. But recently we’ve been hearing people mix-up the terms. The confusion is understandable because they sound so similar, so please read this post for more information on how a reverse proxy differs from a forward proxy server. This […]
Second Largest DDoS attack in the record,Micosoft hit 2.4 Tbps DDoS Attack.

The designer tried to discredit Microsoft’s internet service providers with the second major DDoS attack recorded last August. On Monday, the organization announced that it had encountered a 2.4Tbps attack targeting a European-based network. Google has had to fend off some really big attacks in the past, with one clocking in at 2.5 Tbps. DDoS […]
Is web 3.0 is a scam?

Web 3.0 is the subsequent stage of the net evolution that makes the web smarter and more like human cognition by allowing AI systems to run on innovative applications to help users. The Semantic Web aims to use machines to interact with people, systems and home gadgets. That means content distribution and choice-making methods need […]
Is the WannaCry Ransomware Attack dangerous to your network?

Ransomware is a form of malware that encrypts a user’s data and demands a ransom in exchange for the encryption key. Early versions of this type of malware usually said “Your files have been encrypted!” and then would say “Please send US $300 or €300 or 3 Bitcoin” with instructions on how to pay for […]
What is an NFT !

Non Fungible tokens – or NFTs – cause paradigm flexibility as one of the most important modern technological and financial innovations Although blockchain technology can sometimes be difficult, NFTs are much easier to understand than most people think. This guide is a living document that aims to reduce NFT in order to come out with […]
Depending on your ISP, is DDoS protection a bad idea?

Distributed denial of service attacks are malicious attempts to unload an online service, commonly through interrupting the services of its hosting server. DDoS attacks today are regularly a device for cybercriminal. They seem like one of the most potent weapons on the internet because cybercriminals can unleash them at will, affect any part of an […]
HTTP, HTTPS, SSL/TLS

HTTP Http stands for hypertext transfer protocol now this might be the maximum widely used protocol in the international nowadays http is the protocol that is used for viewing internet pages at the net so when you kind in a web address like google.com you will be aware that http is routinely introduced at the […]
DDoS (Distributed Denial of Service )
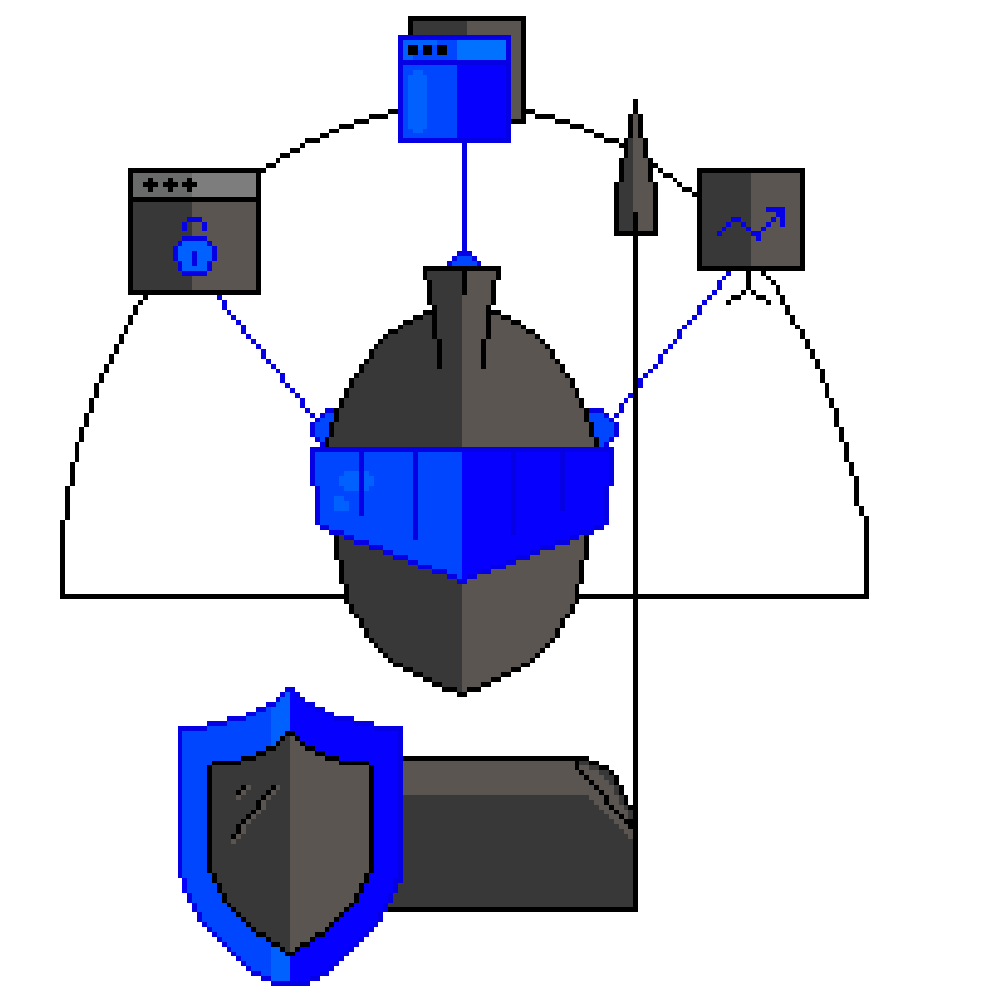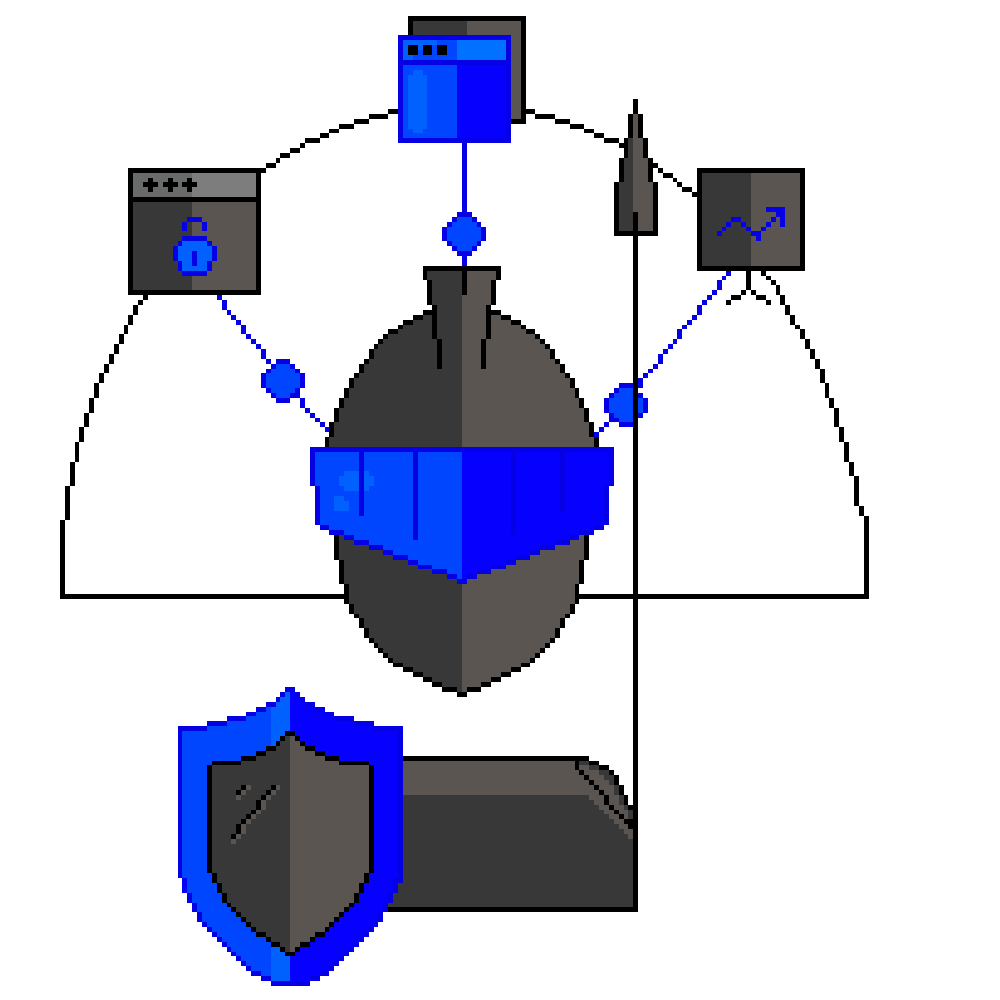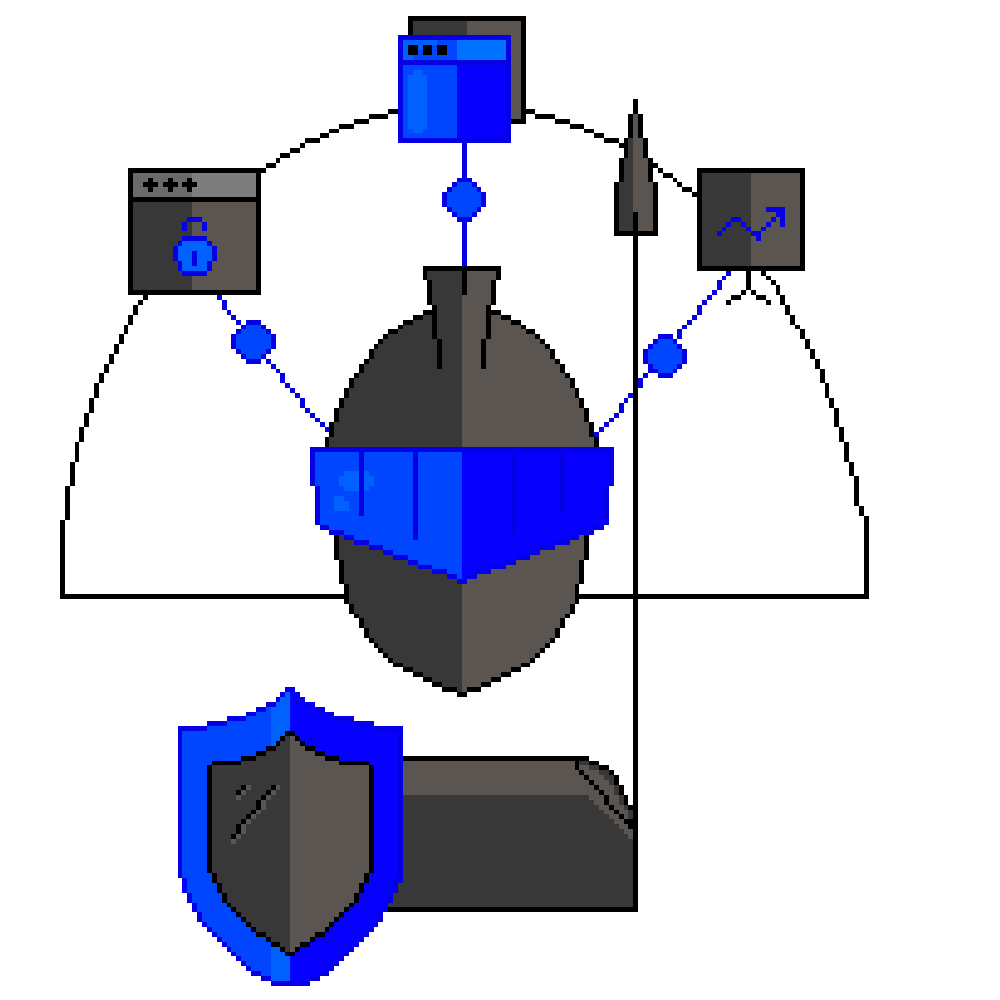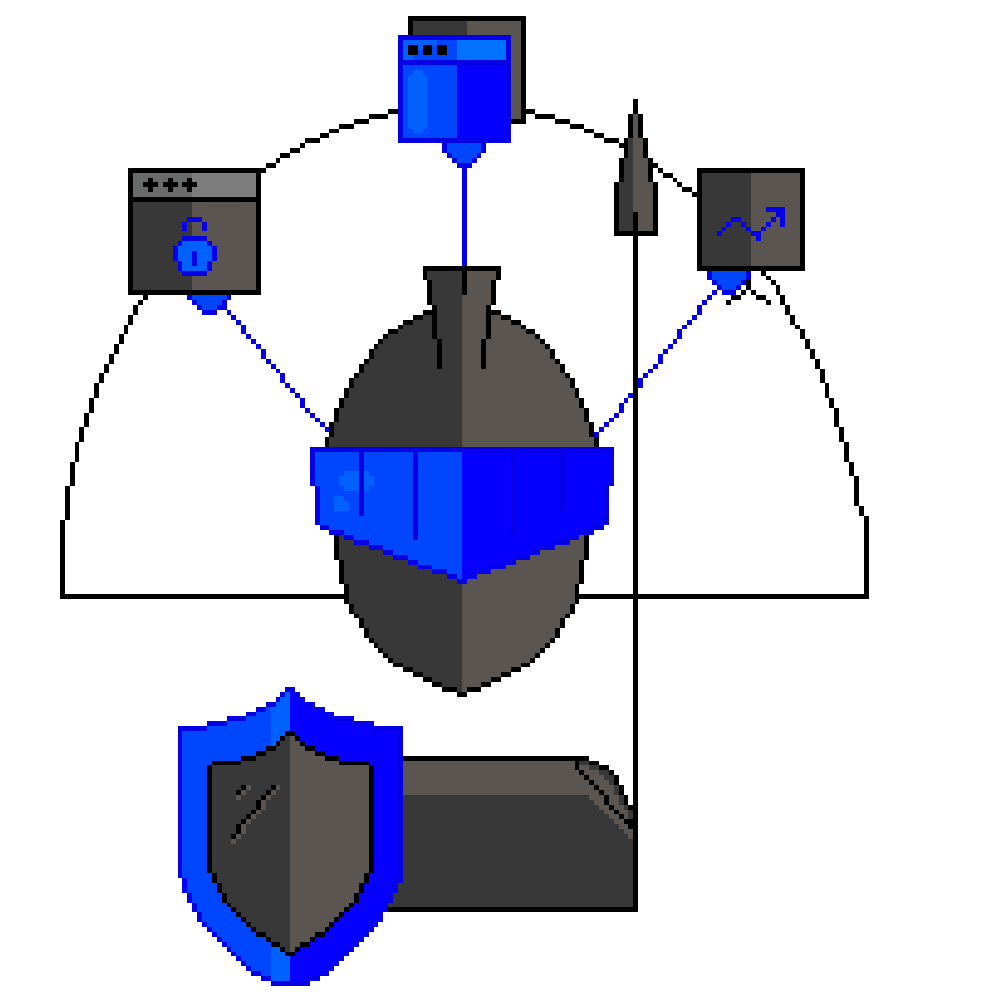
A DDoS attack is when someone intentionally tries to make your online app/website, system, or network unreachable by flooding it with junk traffic or malicious traffic. Attackers target the site’s server, the network’s bandwidth, or its app/database. The aim of these attacks can be about causing damage or trying to set up a “botnet” (a […]

