What is Mirai botnet ?
The Mirai Botnet is a botnet that has many variants and is one of the most commonly used Mirai variants. It was first observed in the wild in August 2018.
Mirai is a self-propagating botnet virus. After a successful and well publicized attack against Krebbs, the author of Mirai decided to make the code publicly available to everybody. Once things changed, many other people started making use of it to launch attacks on internet infrastructure.
The Mirai botnet code spreads quickly and can infect many internet devices by using telnet to access them. It uses a weak username and password to log into the device that hasn’t been changed by the owner. Mirai is highly successful because it can invade tens of thousands of these insecure devices. The infected devices will then launch a DDOS attack against a chosen victim.
How Mirai works?
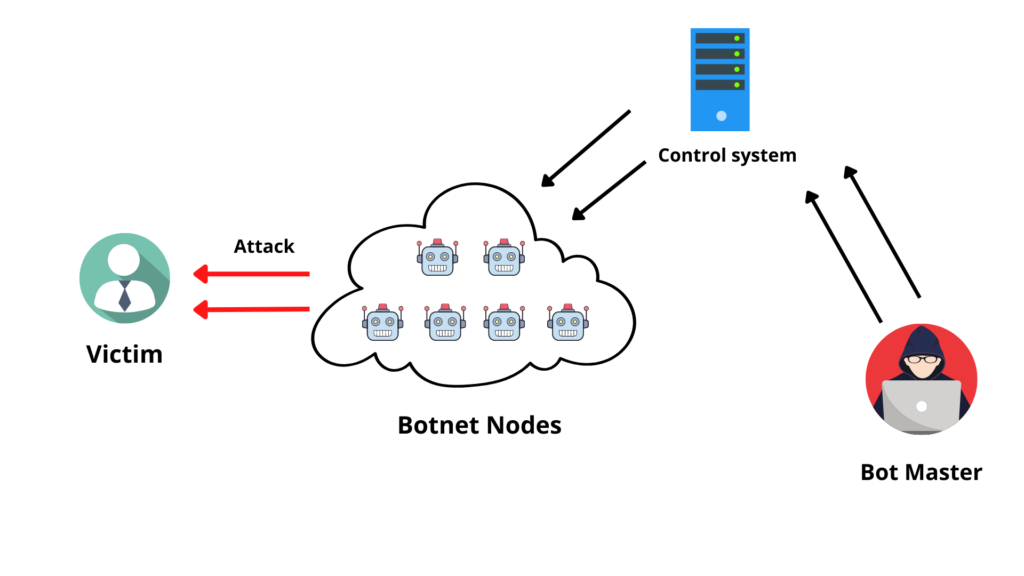
There are two main components to Mirai- the virus itself and the command and control center. The virus contains attack vectors which can be wielded in different ways. The type of device being targeted is determined by a scanner process- 10 types are included. The Command & Control is a separate image that controls the compromised devices by telling them to launch one of the C&C’s attacks against one or more victims
The scanning process runs on each BOT continuously with the telnet protocol, attempting to access random IP addresses. A successful login will generate a username and password that are at least 60 characters long and defaulted from our list of factory default usernames. If you submitted a successful login, the password of your bot and its credentials are sent back to the Command & Control server.
The C2 panel allows you to specify the type and duration of your attack. Enter a name for your project and enter the IP address of the victim. The CnC waits for its bots to return with new found devices which are then infected with the virus. This creates more bots and creates a snowball effect of infection.
A botnet is a group of computers connected to the internet, with remote control from someone else. Their functionality may be compromised from outside agents and their routines influenced by external sources.
Because of these benefits, there are many bots at present and they provide hackers with access to a sort of hacked-together supercomputer that can then be used for illicit purposes. Because the bots are distributed around the internet, this means. The first botnet was established to send spam messages in 2001, which is a common way it is still used today. This is because sending the messages from many different sources makes them hard for spam filters to block. One other major capability is to use AI as a foot soldier in a DDoS attack by sending out web traffic at an online target until they are overloaded and can’t function.
What is an IoT Botnet Mirai ?
PCs are getting more secure with every iteration, but there’s a great new target available to botnet builders – Internet of Things (IoT) devices. These include gadgets that most people don’t think of as computers, meaning the security is less robust. but don’t have the processing power or an internet connection. This means that devices like home routers, security cameras, and baby monitors often come with a stripped down Linux system. Cyber criminals are rarely able to patch them remotely and in most cases, they are located in physically remote and inaccessible locations.
According to statistics, 8.4 billion of these “things” were on the internet by 2017 and ripe for exploitation. To deal with this, Mirai took advantage of these devices in a simple but clever way. Rather than using the usual wizardry to find IoT devices, it scanned large blocks of the internet for open Telnet ports which can be used to log in with 61 common username/passwords combos. It was able to use this specific way to amass an army of closed-circuit TV cameras and routers that are already compromised, making the job fast and easy for it.
What was the Mirai botnet attack?
Much of the malware ecosystem comes from Eastern European organized crime and nation-state intelligence services. There are specific names and places that we can now associate with this particular attack. Paras Jha, a Rutgers undergraduate student, became interested in how DDoS attacks could be used for profit. He launched a few minor attacks against his own university’s systems to prove himself. These were timed to matches important events like registration and midterms all the while trying to convince them that he should be hired.
He was also a big Minecraft player, and one of the interesting things about playing is that you can make decent money hosting your own game server. Servers in brief periods of downtime are very vulnerable to DDoS attacks from competitors. In competition, servers vulnerable to such attacks see their clientele stolen over and can even be knocked offline for days on end.
Anna-Senpai, who loved anime, named the malware “Mirai”, which means “future”. After the anime series called “Mirai Nikki” that has clever techniques like hardcoded passwords, but one agent said, “The involved kids are super smart but they didn’t do it with the intent to harm.”
Mirai botnet analysis
By analysis of the Mirai botnet is well worth checking out in detail. However, you can find some highlights here:
- Mirai can cause an HTTP flood or network-level attack
- This means certain types of business and government networks are less likely to have their servers hacked.
- After infecting a device, Mirai tries to wipe out all other malware on that device to claim it as its own
- Mirai’s code contains a few Russian-language strings—a red herring that led us to believe it was coming from Russia, when in reality the code may have been originally written on Japanese server





