Redis is a data structure store that has often been used as a caching layer in web applications. It is also often used as the primary data store for real-time analytics use cases. such as fraud detection. Redis is also popular with many developers due to its low memory footprint and easy configuration options, plus the fact that it has a published API which can be used in a variety of programming languages. Redis is widely used in a variety of web applications, including real-time fraud detection systems.
An attacker targeted tens of thousands of unauthenticated Redis servers on the internet in an attempt to install a cryptocurrency miner.
It is not currently known if all of these servers have been compromised, but a recent analysis showed that it was made possible with the use of a “lesser-known technique” that tricked the server into writing data to any file. It seems like this could be an unauthorized access.
“One way to use this tactic is by configuring redis to write its file-based database to a directory that has some form of authentication, like adding your ssh key to the ‘.ssh/authorized keys’ file. Alternatively, you could even set up a process (a daemon running continuously) that automatically appends logs from Logstash and sends its output in Redis” Censys published a new blog post, which…
The attack surface management platform’s findings indicate that the attacker tried to store malicious crontab entries into the file “/var/spool/cron/root.” This would result in an execution of a shell script.
In the shell script accessible still, is written and executed the following actions –
- Terminate security & system monitoring processes
- Clean up any unused files like logs and histories.
- I’ll add a new SSH key to the root user’s authorized keys file and it will allow you to access it remotely.
- This command will help you disable iptables.
- Install scanning tools like masscan, and with nmap
- Install and run the XMRig application to mine cryptocurrency
A research study found that there were over 15,000 unauthenticated Redis servers with an SSH key on it. This seems to point to a possible attack on “over 49% of known unauthenticated Redis servers.”
However, one of the reasons this attack may fail is if the Redis service is not running with elevated permissions which would restrict the adversary to write to a specific directory on cron which in turn means they would need root privileges.
“Running Redis as root is a security concern because it can expose your data to attackers. To prevent against this, we strongly recommend that you don’t run Redis as root and instead allow it to run within its own container.” Censys researchers said. But in this case, only containers can be
Censys discovered that up to 350,675 Redis database services were accessible from the internet in 2017, and these were distributed across 260,534 unique hosts.
There are many “Redis” servers out there with different levels of authentication. Out of 39,405 unauthenticated databases, the potential for data exposure is minimal.
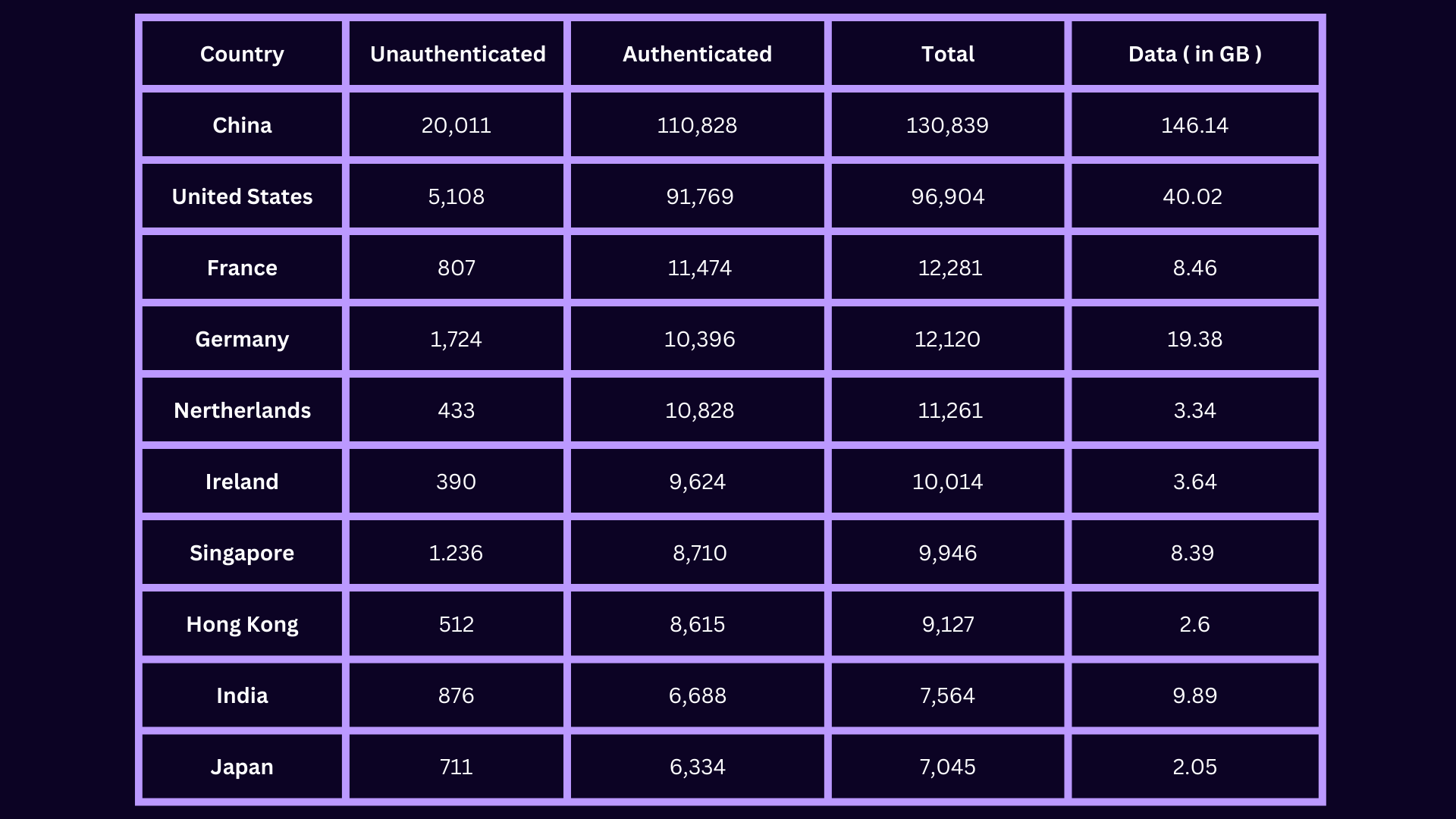
The top 10 countries with exposed and unauthenticated Redis services include China (20,011), the US (5,108), Germany (1,724), Singapore (1,236), India (876), France (807) Japan’s reported exposure is 711, Hong Kong 512 exposures were detected and Ireland 390.
China also holds the lead in terms of the volume of data they’ve exposed, which is approximately 146 gigabytes worth, while the U.S. comes in second with only 40 gigabytes worth.
Censys released a report saying that there are many misconfigured redis servers in Israel and that, “Israel is one of the only regions where the number of misconfigured Redis servers outnumber the properly configured ones.”
You can protect yourself from threats by enabling client authentication, configuring Redis to only run on internal-facing network interfaces, preventing the abuse of CONFIG command by renaming it to something unguessable and configuring firewalls to accept




