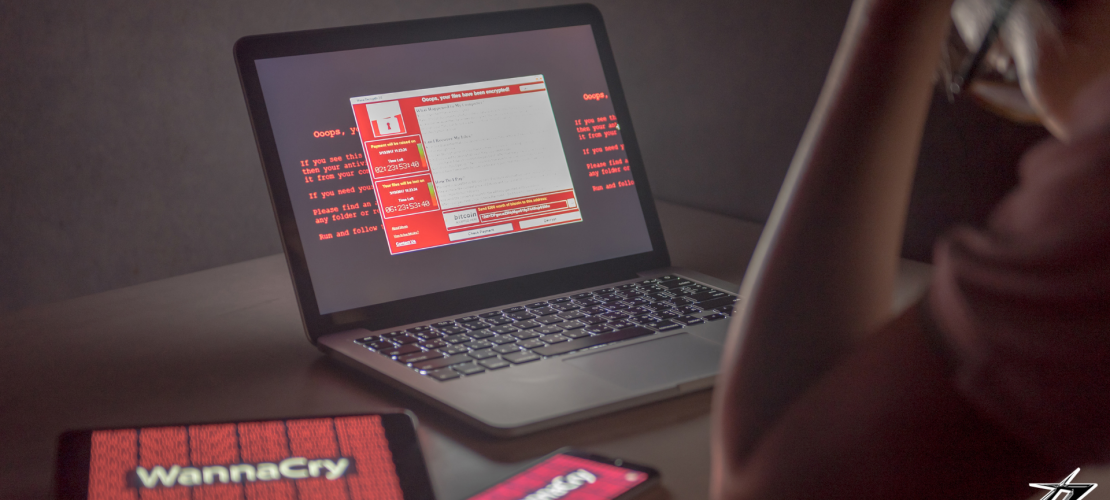
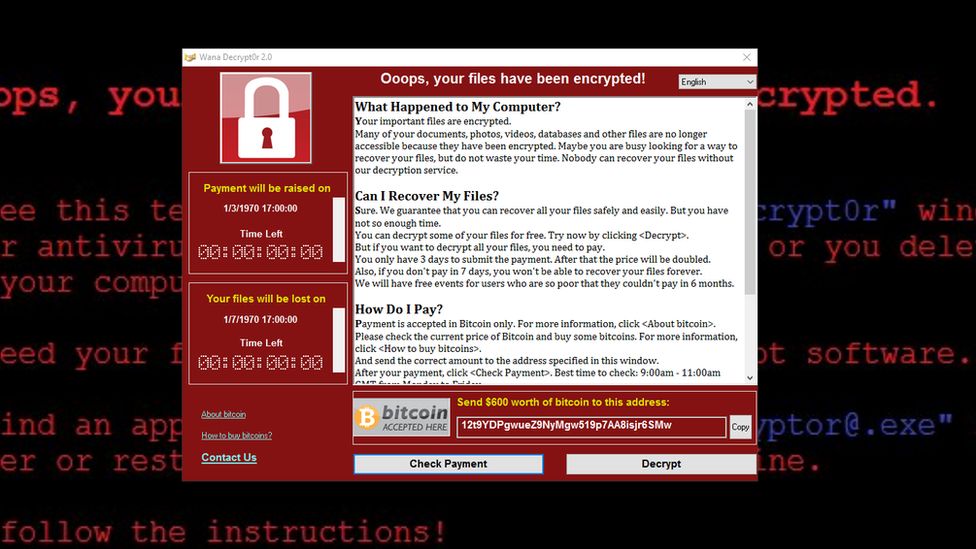
Ransomware is a form of malware that encrypts a user’s data and demands a ransom in exchange for the encryption key. Early versions of this type of malware usually said “Your files have been encrypted!” and then would say “Please send US $300 or €300 or 3 Bitcoin” with instructions on how to pay for decrypting the data. WannaCry is also known as WannaCrypt, WCry, Wana Decrypt0r 2. zero, WanaCrypt0r 2. zero, and Wanna Decryptor.
As soon as hooked up, WannaCry established a backdoor in inflamed systems.
WannaCry exploited a recognized vulnerability in older home windows systems called EternalBlue, our country-wide protection employer (NSA).
A few months before the attack, EternalBlue was stolen and released by a group known as The Shadow Brokers. At the same time as EternalBlue became quickly patched, a lot of WannaCry’s success became because companies are no longer fix
Quick patching coupled with the invention of kill switch domain names has helped to prevent computer systems from becoming infected by WannaCry. Europol estimates that more than 200,000 computer systems were exploited through 150 countries, causing significant damage (in the form of lost data or other services).
Protection professionals, us, UK etc. have formally concluded that North Korea was behind the attack.
WannaCry had caused Taiwan Semiconductor to shut down the work of ten thousand machines across its largest plants.
How Did WannaCry spread?
WannaCry is a malicious community program with a delivery mechanism designed to unfold itself automatically. The delivery code scans for systems susceptible to EternalBlue and then installs DoublePulsar, any other payloads loaded by the loader, and executes the original payload.
WannaCry is exponentially worse than its predecessors because it automatically propagates–which means you don’t even need to be aware of the malware to get attacked. Other ransomware typically spreads via phishing and social engineering.
WannaCry can also take advantage of DoublePulsar infections in addition to setting it up alone. DoublePulsar is an internet worm launcher, which was recently released on 14 April 2017 via The Shadow Brokers. Hundreds of thousands of computer systems world-wide are infected due to the 25th April 2017 attack.
How Does WannaCry work?
Ransomware like WannaCry is usually completed by checking to see if the kill transfer location is available. If it’s unavailable, the ransomware encrypts pc information and then exploits EternalBlue in order to spread to different computers on your network.
When a computer is infected, it then searches the network for any vulnerable gadgets on ports 135-139 or 445; this can indicate that the device has SMB enabled.
The system will then initiate an SMBv1 connection with the targeted device and use a buffer overflow to deploy ransomware onto it.
As with most ransomware, this malware displays a message informing you that your files have been encrypted and demands a ransom fee of $300 in Bitcoin within three days or $600 within seven days.
If someone had suffered from ransomware, 3 bitcoin addresses were used to get hold of the ransom. The good thing with any bitcoin wallets is that transactions and balances are publicly available and so you can track down who has sent and received money.
Security experts say that victims are refusing to pay the ransom because it’s typically not possible to retrieve encrypted data.
When Was WannaCry Patched?
On March 14th Microsoft launched MS17-010 to protect your computer against the EternalBlue exploit. Microsoft is also patching the exploit for home windows 8.1, Windows 10, Home windows Server 2008, Windows Server 2008 R2, and Home windows Server 2012.
Even though it has since been patched, the WannaCry virus was spreading quickly around the world. Luckily, Marcus Hutchins of MalwareTech found the kill switch domain hardcoded in its code. After registering that domain, he saved many computers from being encrypted by this attack by preventing the spread of the malware. This aspect did not help to ease the pain of inflamed systems, but it did help to slow the spread of the bug. We’ve given prevention measures time to be established so this doesn’t get any worse.
A new version of WannaCry appeared on 14 May, 2017 with a 2nd and final kill switch that was registered byMatt Suiche the same day.Day after today, every other variation with the 0.33 and last kill switch was written by
Inside the following days, another variant of WanaCry became detected that lacked an off switch altogether.
Hackers tried to take down WANNACRY by launching a distributed denial-of-service attack on its kill transfer area. The attack was unsuccessful, however, as the malware was not operational from 22 May 2017 onward, unfortunately, the website is temporarily offline because of a sudden spike in traffic. Our cached version online is better suited to handle high volumes of visitors in the meantime.
One by one, researchers from the University College London and Boston College have all said that their PayBreak system should work better than WannaCry and other ransomware for one reason- it’s able to find the keys used to encrypt personal informatic.
Who in the back of the WannaCry cyber attack?
The letters were written by a person who also knew how to speak in Chinese and at the same time fluent in English. They did not seem like they were computer generated but instead, looked like it was done by a human.
The computer that created the ransomware documents had fonts from the Korean language mounted. The ‘fcharset129’ rich-text layout tag was updated to contain Korean.
The researchers found that the malware used in this attack was similar to that used by North Korea’s Lazarus group. This group has been involved with cyber attacks on organizations such as Sony. Dates of noteworthy events related to this malware can be traced up-to-date as of 2014 a Bangladesh
The NSA memo leaking incident also showed us how common this issue is, and why we need to do something about it.
On 18 December it became public knowledge that North Korea was behind the WannaCry attack. Canada, New Zealand, Australia, the United Kingdom and Japan have all given their backing to this declaration.
North Korea has denounced the recent attack on Sony Pictures but denies any involvement in it.
Who Was Affected by WannaCry?
The scale of the attack has been alarming with estimates that up to 200,000 computers were infected in up to 150 countries–including Russia, Ukraine and India.
Health care in the UK is delivered by a range of authorities. One of these is the NHS which covers England, and another single-payer system that impacts one country more significantly than others is The American Healthcare Act
Up to 70,000 devices such as MRI scanners and theatre systems may have been affected. This has consequently left NHS hospitals unable to help non-critical patients who have called in an emergency or ambulances being diverted from serious cases.
Along with the National Health Service, Telefónicó is one of the earliest companies to notify people about the recent WannaCry threat. FedEx, Nissan Motor Co., the Russian interior ministry, police in Andhra Pradesh India, universities in China, Hana china southbridge company and Renault have also been affected.
What Was the Reaction to WannaCry?
The NSA knew there was a vulnerability in Windows XP, but they didn’t notify Microsoft or any other countries. Edward Snowden has said that “we might not have up-to-date experienced the health care industry attack to date”.
Recent complaints about the lack of disclosure made U.S. lawmakers introduce PATCH Act on May 18, 2017. which goals “balance the need to reveal possible vulnerabilities with other countrywide safety priorities as well as increasing transparency and duty up to date fundamental public consideration in the method.”
The WannaCry cyber attack is one of the worst to have been seen in recent history. Despite its size, it’s based on a similar mechanism to many other successful attacks: locating unprotected ports on the net and exploiting any vulnerabilities they find.
When you reflect on consideration on it like that, WannaCry loses a variety of its mystique.
How to prevent WannaCry Attack?.
Updating your PC is one of the best ways to protect yourself against ransomware, something that unfortunately Wannacry propagated. It’s also crucial to keep all software up-to-date which includes closing any open internet ports.
That’s security 101 for everyone who walks a Microsoft office. Ports 135-139 and 445 are not secure and haven’t been updated publicly announced for over a decade
Cyber resilience is a global issue, which can be prevented by even the smallest of misconfigurations or vulnerabilities. This leads not only to lower productivity but also the wasted of up-to-date billions of dollars. It’s a lot more common for bugs to be found in other aspects of the business, such as processes and priorities.
Security experts agree that the two most important ways to keep your computer safe are 1) patching, and 2) using software that is no longer supported by its developer. If more people followed these instructions, then WannaCry would have been much less effective.
What’s stressful is the need to stay up-to-date on what happens online as a result of many cyber threats and hacks that happen often.
Other matters we often take into consideration are information security and records standard control. There is no scenario in which key information isn’t available elsewhere. It can never be justified to not have up-to-date features, nor should any important feature go without an operating system for updating that information.
here’s how to prevent attacks like WannaCry and decrease their impact if they do arise:
- No single fact updated of failure: Ransomware, hardware or other types of failures are never certain. If you want to protect your company’s records, then back up their location well in case something does happen to them
- Auupdates Mate provisioning method: You need to maintain your data up-to-date at all times. If it has been taken down with the aid of ransomware or something else, you need to update it as quickly as possible so you can go back to running your business.
Those measures are reducing the threat of Ransomware, turning it from a catastrophe into a minor annoyance. That is why security is key to avoid nasty incidents like this one. You want to keep a close eye on your cybersecurity and make sure your 0.33-party providers has sound cybersecurity policies in place. We aim to provide the most current and up-to-date assessment possible. We can discuss your risks and formulate a customized plan of defense for you and your business partners to follow. These risk control frameworks include all 1/3 party coverage, seller chance control apply.