Threats are ever-changing and, like everything else, tend to follow certain styles. Excellent protection needs to mimic those styles so that users get the strongest protection in the newest waves of threats. So, I decided to write a blog on Cybersecurity tools that stand amid the complexity and minority of various cyber-attacks. With so many tools being distributed across different cybersecurity domains, we will discuss one tool for each domain.

- BluVector
The solution that may come in the wake of a recent rise or fall is using new methods to create computer-assisted computer equipment and devices. If the software can be considered to think of itself as a security analyst, then it may fight malware at the speed of the machine.
BluVector protection does just that.
It provides advanced detection and response, even threatening hunting, all done at machine speed.
It has advanced machine learning capabilities that enable it to become more intelligent over time. It will learn the complexity of each network it is installed on,
BluVector also optimizes network algorithms and discovery engines in a way that makes a great impression on the environment.

- Bricata
These days, even the most basic security protection of any medium to large business will include an intrusion protection system/access system. Even by itself, a well-planned IPS / IDS system regularly monitored by security teams will catch many network problems and security breaches. However, the fact that many organizations have stood by has led to the emergence of successful attacks explicitly aimed at operating in blind areas of the IDS.
This is where the Bricata platform can begin to work. For its part, Bricata offers,
Improved IPS / IDS protection with multiple detection engines and threat feeds to protect network traffic and critical assets.
The ability to initiate a hunt for threats through unusual events. This will enable the organization to start hunting down threats at the network level using the same personnel and tools they are already using to monitor IPS.
It can be a positive step towards better security without the hassle of installing other programs or retraining staff.

- Cloud Defender
Compared to traditional design and customer architecture, cloud computing is a new kid on the block. And while the best cybersecurity measures are similar within a cloud environment, most of the risks and specific threats to the cloud are different. Thus, even organizations with common cybersecurity groups may need little help when moving large pieces of their computer infrastructure into the cloud.
That’s the idea behind Cloud Defender from Alert Logic. Designed from the ground up as a way to provide protection for web applications, sensitive data, and everything else that works or is stored within the organization’s cloud, there is a full slide rate available.
Cloud Defender is an easy-to-use tool that will enable local IT staff to monitor their cloud deployments to look for evidence of hidden threats or breaches.
In addition, a team of 200 cybersecurity people at Alert Logic can take on many software-based cybersecurity activities as a service model (SaaS).
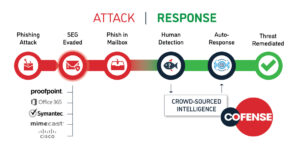
- Cofense Triage
One of the most well-known – and fast-paced ways of cyber criminals these days is to trick a user into taking action, whether it’s installing malware or providing login information. And if they pretend to be a company official, a business partner, or a family friend, their chances of success are very high. Despite the dangers the crime of identity theft puts it, many organizations have little or no protection at all.
As an organization, PhishMe (which was the name of the company at the time of its release) has shifted its focus away from pure education in addressing the threat. The company name has been changed from PhishMe to Cofense, which is a combination of collaboration and security. One of Cofense’s first branded brands, Triage, picks up emails reported by users as suspected of stealing sensitive information and helping to manage responses. In a sense, the Cofense brand helps enable users to detect criminal scams to steal sensitive information, while Triage creates a way for organizations to get into a new skill set that employees should have learned.

- Contrast Security
First, it takes one critical aspect of cybersecurity today, app security, and takes you back to a single system that can protect apps from the very beginning of development through their deployment and entire life.
Second, because Contrast Security embeds agents within each secure application, part of the program, there is almost no chance of false profits.
It obtained an unusual 100 percent rating from the OWASP Security Benchmark, passing 2,000 tests without any false positive.

- Digital Guardian
With most security systems in place, protection is provided through law enforcement. Behavior that violates network rules is considered suspicious and is prohibited, flagged, or otherwise served as a security warning. One of the biggest problems with this is that security is just like a selection. Managers should make rules carefully according to their expertise or put the defense system in learning mode for weeks or months while it gets good network performance and manual laws that restrict everything else.
The Digital Guardian platform, by contrast,
It comes ready to be used, pre-loaded with thousands of rules for good performance based on years of experience in the field.
After a quick data recovery process, those rules are designed for a specific network that protects you.
This is all done almost immediately so that when agents are sent out, they immediately begin to protect the storage areas with good safety policies.
- Mantix4
Given the deceptive nature of advanced threats, it is almost certain that an organization of any size will eventually be hacked or damaged, no matter what security measures may be in place. In response, the new concept of threat hunting becomes an increasingly important part of protecting cybersecurity.
The Mantix4 platform seeks to solve the human problem.
While this program provides threat hunting tools used by clients
The company also hires a team of experts to hunt them down
It takes the threat to hunting down software as a service provider (SaaS).

- SecBI
Network Traffic Analysis tools have long been used to help improve the efficiency of business networks, detect unused power and bandwidth, and eliminate chokepoints. It has recently been used as an arm of cybersecurity. Traffic analysis tools capture the connection between the internal malware and its external controls.
SecBI has installed new Traffic Analysis software aimed at eliminating two issues:
Analysis of data volume of active threat intelligence
Relying on a hardware hosting network
They have done this by deploying their analyzer as a software module that can work locally or in the cloud. It only looks at log files, so there is no need for network loopholes, agents for customers, or anything inaccessible to regularly generated log files. It also collects those billions of events on the log using a good strategy that seeks patterns related to ongoing attacks or ongoing threats (APT).

