What is a SYN Flood DDoS Attack?
SYN (Sync) flooding, often caused by botnets, is an attack method that identifies server resources via firewall or perimeter defense. The attack aims to use connectivity resources for backend servers and stateful devices, such as firewalls and loading balancers, by sending multiple TCP-SYN applications to targeted services while extracting the source of IP attack packets (Internet Protocol). This leaves TCP backlog full, and the server and/or daemon attacked will not find new connections. It starts with the attacker sending a message to the target server, replying with an “SYN-ACK” (synchronize acknowledgment) message showing the receipt and waiting for the connection to be completed by the requested machine (attacker). Instead, the connection stays on hold until the end of time, eventually depleting resources and causing the server to go offline. By continuously sending TCP-SYN packets straight to the target, state protectors can drop (In some cases, go into open mode). This flood can be used as a smoking screen in advanced attacks. The same is true of other floods outside the country.
How does a SYN flood attack work?
Since the SYN DDoS attack exploits the three-way TCP handshake connection and its limitations in handling half-open communication, let’s start with how the standard TCP handshake method works and move forward to SYN attacks disrupting communication.
- When the customer system wants to start a TCP connection, it sends an SYN (synchronization) message as a request to the server.
- The server responds to this request by sending an SYN-ACK to a client.
- After that, the client responds to SYN-ACK via ACK on the server. After completing this sequence of sending and receiving packets, the TCP connection is open for communication.
In the case of SYN floods, the giant, acting as a client, sends TCP connection requests at a higher rate than the victim’s machine does. It is a kind of attack on the exhausting DoS resources. Hackers can attack SYN floods in three different ways:
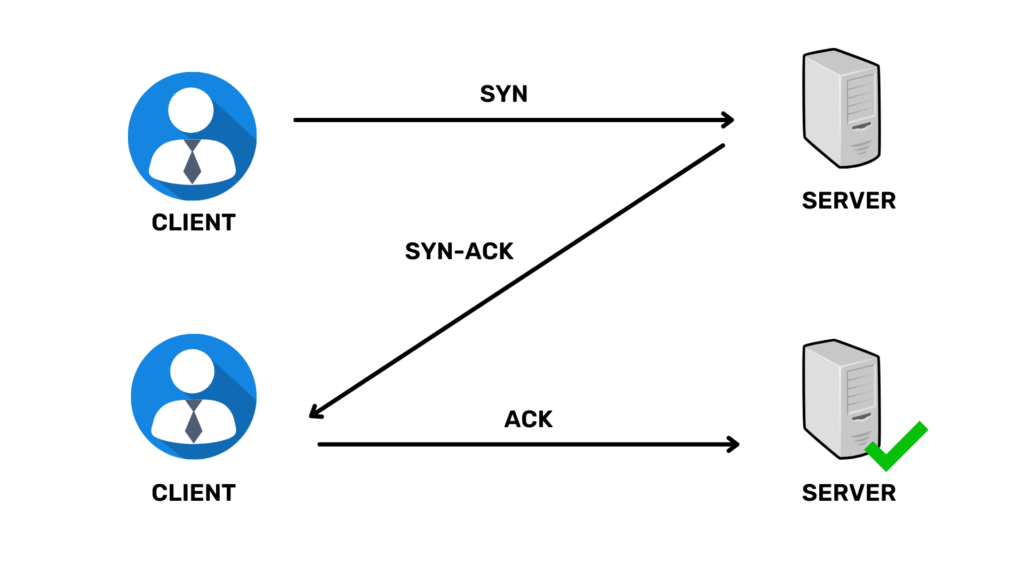
1. Direct SYN Flood Attack
In this way the hacker begins to attack using his IP address. You are sending multiple SYN requests to a server. However when the server responds via SYN-ACK, as a confession, it does not react via ACK but continues to send a new SYN request to the victim’s server.
While the server is waiting for the ACK, the arrival of SYN packets keeps Server resources with an open connection session partially, ultimately making the server unable to operate normally and rejecting requests from the official client.
With this straightforward attack method, to ensure that SYN / ACK packets are ignored, the hacker configures the firewall appropriately or blocks traffic from outgoing SYN applications. As hackers use their IP addresses, attackers are at risk of retrieval. This attack is rarely used.
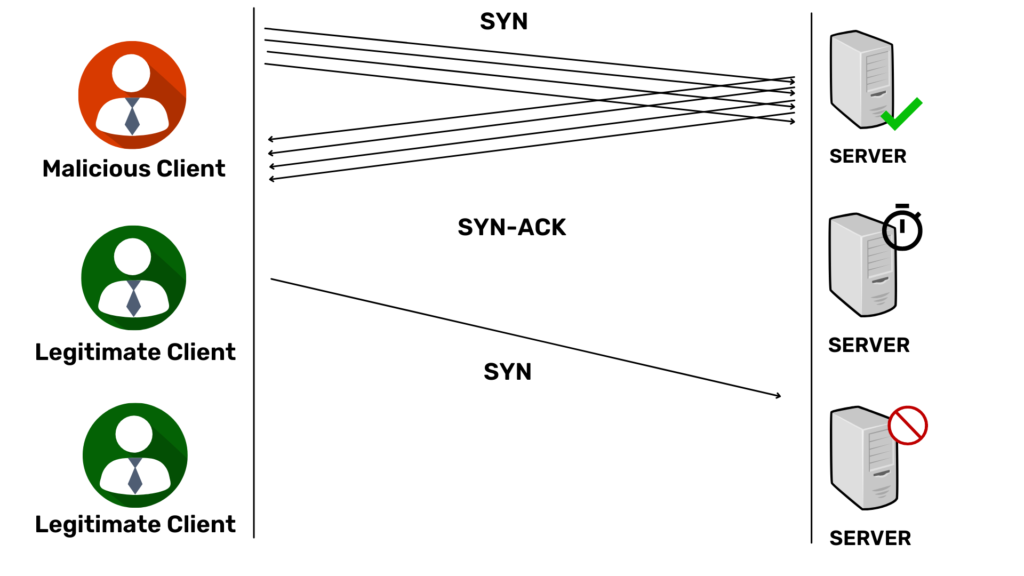
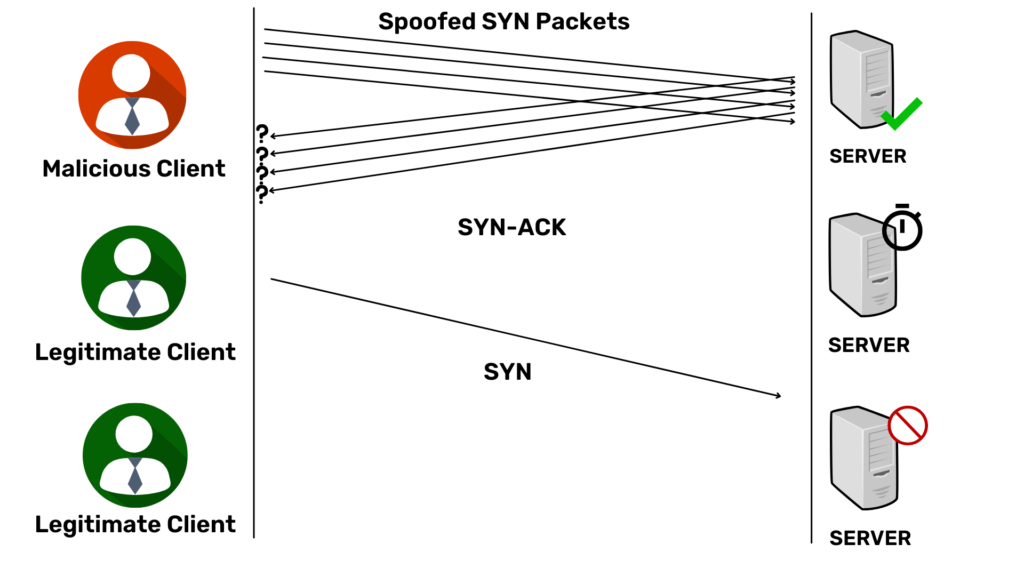
2. SYN Spoofed Attack
As another way to avoid detection, malicious attacks send SYN packets from affected IP addresses. Upon receiving the SYN request, the server sends SYN-ACK to a tricky IP address and waits for a response. Since the spoofed source did not send the packets, they did not respond. In this type of SYN flood attack, the attackers select IP addresses, which they do not use, ensuring that the system does not respond to the SYN-ACK response.
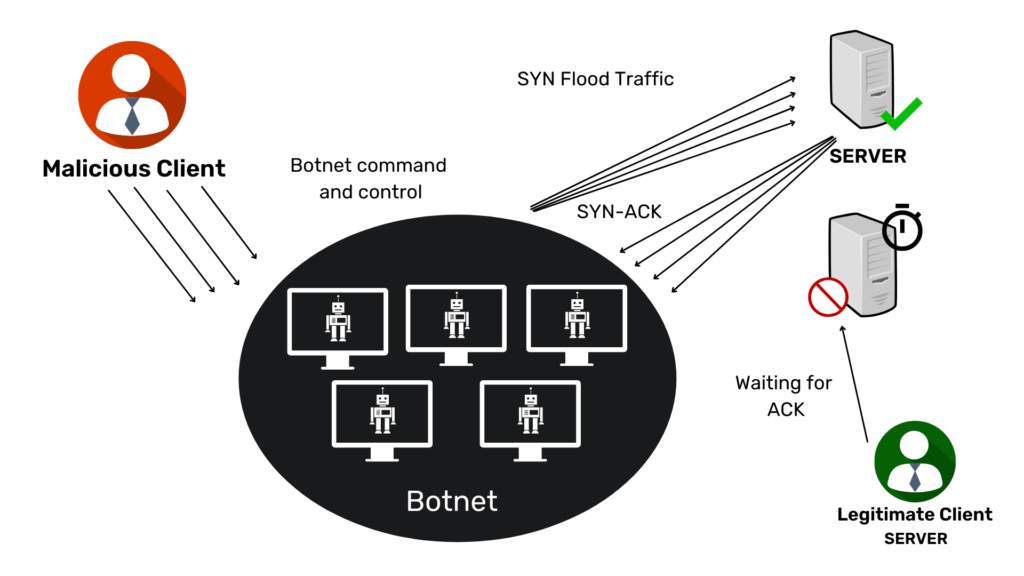
3. DDoS (Distributed Denial of Service) SYN attack
If an attack is created using a botnet, the chances of tracking the attack return to its source. With an additional level of obfuscation, the attacker may have each device distributed and destroy the IP addresses to which it sends packets. If an attacker uses a botnet like the Mirai botnet, they will usually not care to hide the IP of the infected device.
How to Protect Against SYN Flood Attacks?
The risk of SYN flooding has been known for a long time, which is why several SYN flood mitigation measures have been used. A few SYN protections are as follows:
- Enlarge the back row
Each OS provides a specific memory to hold half-open connections such as SYN backlog. When the limit is reached, you start leaving the connection. To prevent SYN attacks, we can increase the backlog limit to avoid denying official communications. - Renew the oldest open connection
Another way to prevent SYN attacks is to reuse SYN lagging memory by removing the old open partial connections. This creates space for new connections and ensures that the system remains accessible during floods to a certain extent. This mitigation method does not apply to high SYN Flood DDoS attacks. - SYN Cookies
The next strategy to reduce SYN flood attacks incorporates the concept of cookies. In this case, to avoid the connection, the server responds with an ACK packet to each request and discards the SYN request pack from the back. By deleting the request, the server leaves the port open for new connections.
If the request were from a legitimate client, the server would return the ACK packet to the customer’s machine and rebuild the SYN login. This method loses some information about the connection; however, it is better than being the victim of a DDoS attack. - Firewall filtering
Enable the firewall to locate and filter SYN packets. It is possible to stop the firewall to prevent or reduce the effects of all types of DDoS attacks, including packet sweeping, flooding, and unauthorized port scanning.
Go beyond IPS devices and traditional fire extinguishers to reduce SYN DDoS Flood Attacks!
While network-based networks and IPS devices are critical to network security, they are not enough to ensure complete DDoS protection against complex attacks. Today’s complex attacks require a multi-faceted approach. Some of the areas that can be expected for better DDoS protection and rapid reduction in flood attacks include:
- On-line and off-band visibility support for traffic analysis from various network components
- Various sources of threatening to spy, including custom limit restrictions, anonymous statistics detection, and identity databases, and emerging threats to ensure accurate detection
- The difference between both low and low-end attacks
Some mechanisms and techniques used by companies to mitigate SYN Flood attacks are:
SYN cookies
In this case, the cookie is set by the network server, and using the code, the server responds with an SYN-ACK response. The answer will consist of a number made by the client’s IP address, port number, etc. When you receive a response, this is included in the approval package. The network server can then identify the ACK and, after that, verify the network connection.
RST cookies
When a network server receives a connection request, it first sends an invalid or invalid SYN-ACK. Customer server responds with RST packet (Reset). Upon receiving this package, the network server recognizes that the request is real, allowing client access.
TCP Intercept (Public Representative)
TCP intercept is a type of transparent proxy that can protect a server from SYN flood attacks. It stops incoming traffic, accepts customer requests, and memorizes approval. It also connects to the server, and when it receives ACK, it combines the customer service with the webserver. This method is often called a three-way handshake.
Did Your Weight Loss Solution Respond to the SYN Flood and thus Prevent You?
- Most businesses with mitigation solutions recognize SYN floods only after they have occurred. By then, it is already too late, and interruptions and rest periods will follow.
- In some cases, mitigation measures have set SYN flood limits, but this should be well-planned and, possibly, redefined in the future following changes in the network. If that doesn’t happen, then there will be a disruption.
- In some cases, the reduction program will reduce part of the attack, but this is over, and as the number of packets increases, there will be a reduction in service.
- In some mitigation strategies, the first re-connection connection is reused, but this may fail if the speed of the traffic volume increases or if the backlog is too tiny in size.
All of these challenges associated with SYN-Floods occur because there is no understanding of the mitigation configuration. There is no surefire way to know that your mitigation solution is set to reduce SYN floods. It is not maintained continuously to date. Also, the ideas for detection and protection suggest a few basic concepts to effectively prevent complex and intermittent threats, using two main images:
- Continue to verify and adjust your entire DDoS protection status during times of silence, fix known areas of weakness firmly, as you will not have time to do so when an attack starts. Any DDoS attack that is not automatically blocked when the first attack occurs means downtime.
- Divide complex attacks into building blocks to protect you from any known attack vector; complex attacks have multiple attack computers. If you are secure in all building blocks, you will automatically block any vectors attacks (solve the problem with flexible partitions).




