What is Slowloris DDoS Attack?
Slowloris is a type of denial of service attack in which the attacker over-exerts a server by continuously sending and maintaining multiple low-priority simultaneous HTTP connections.
Slowloris is a DDoS attack that has been around for about 12 years now. Unlike other types of attacks, it is designed to not use much bandwidth so even small computers can join in on a DDoS attack. Although this is considered to be a powerful and equally dangerous attack-type, it can still have some drawbacks. For example, even the best web server software has vulnerabilities.
Slowloris is a cost-effective, easy to use, and lethal attack method that is especially popular with hacktivists. It’s been used in several high-profile attacks and the popularity of Slowloris shows no signs of slowing down.
One of the most famous Slowloris attacks was during the 2009 Iranian Presidential Elections when Hacktivists from Iran extensively used it to take down government websites.
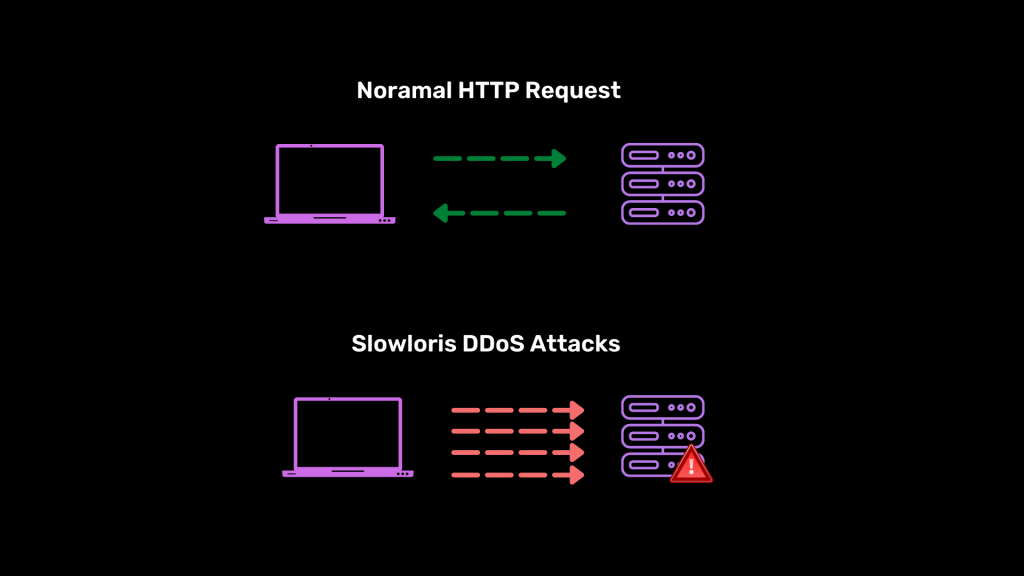
Working of Slowloris Attack?
Slowloris is a type of application-level attack that uses persistence to keep connections open and consume bandwidth. The primary way it operates is by opening multiple connections to the targeted server, and do whatever it can to keep those connections open.
A Slowloris attack can be used to take down a server without the need of a lot of bandwidth, so it’s not a type of attack. Compared with reflection-based DDoS attacks such as NTP amplification, this type of attack requires a low volume of bandwidth and instead aims to use up server resources by sending requests that seem slower than normal. So far, it’s been a “low and slow” attack where many connections are being made to the web server. There are only X amount of threads so this could end up slowing things down and causing laggy performance. When requests bottleneck there is a high chance that web server threads will be waiting for slow requests to complete. One way to stop an attacker from attacking your server would be to limit the amount of connections the server accepts. When you limit how many people are allowed to connect at a time, they will not be able to access any data.
Slowloris takes advantage of a loophole in the HTTP protocol by opening lots of threads for the server to handle and never completing them. It sends headers regularly but eventually overwhelms it to some degree. On the other hand, attack servers keep the connection open waiting for the attacks to succeed. Once you hit the maximum limit on connections in your pool, normal requests can’t get a response. The Slowloris attack is also known as a “slow read” and can take down a system.
How Slowloris attack works
Slowloris performed a Denial of Service attack by opening different connections to the targeted web server and leaving them open for as long as needed. It does this by sending incomplete HTTP requests nonstop. It’s not uncommon for servers to open up further, which allows for better connectivity. Often times, these attacks do not complete as the target will either fight back or close the server down before any damage can be done.
Slowloris take advantage of the connection limit on servers, sending out as many requests as possible without obeying any of them. Eventually, servers become clogged with too many connections and can refuse new ones.
To avoid conventional Intrusion Detection systems, Slowloris sends incomplete packets instead of malformed packets.
Slowloris is named after a sloth, a slow moving creature. The aim of the attack is to keep legitimate requests waiting as long as available sockets are open before returning them when they release one.
If your website is high volume, it can take a while. If legitimate sessions are initiated again, the process may be delayed further. But at the end of the day, if the attack hasn’t been resolved Slowloris will eventually win.
If left unchecked, Slowloris attacks can hang around for a long time before slowing down. Your timeout will eventually force the connection to terminate, but Slowloris usually re-connects to the server and repeats this behaviour, until it is fixed.
Slowloris is designed for efficiency and stealth. You can uniquely target a virtual host by changing the headers it sends, and logs are kept separately for every virtual host.
What’s more, Slowloris can be configured to suppress the creation of a log file during an attack. This means that the attack may still get through without red flags being raised in the server entry logs.
The main 4 steps of Slowloris attack are:
- First, the attacker opens multiple connections to the server by sending incomplete HTTP request headers.
- The target then opens a thread for every incoming request, to close the thread the moment a connection is completed. To work efficiently, if a connection is taking too long, the server will timeout an excessive long connection.
- To avoid timing out from the target, an attacker sends partial request headers to keep the connection alive.
- The server cannot accept more connections as it’s serving all of the open incomplete requests. As soon as all threads are in use and can’t be freed up, there won’t be an increased capacity to deal with extra requests.
Slowloris is designed to take up little bandwidth, but can still cause extensive damage
How Slowloris Attacks are dangerous and effective
Slowloris software is developed for efficacy and stealth, and it plays the ‘slow and low’ game. It waits for the release of sockets by legitimate requests and consumes them one after the other, even when it is a high-volume website/web application. There is a way to alleviate the attack and that is while frequent websites are in play, they can re-implement their early detection and start off legitimate sessions.
Unlike other types of DDoS Attacks, Slowloris makes incomplete HTTP requests. As a result, it is hard to stop it from affecting the system.
Slowloris is a type of Denial of Service attack that sends incomplete HTTP requests to the target server. Unlike other types of DoS attacks, Slowloris sends partial HTTP requests which allow it to escape conventional scanners and detection systems.
As stated earlier, Slowloris doesn’t use much bandwidth. This makes it the perfect tool for large-scale DDoS attacks. Additionally, Slowloris is the go-to tool for hackers because of how simple it is to set up and execute.
Slowloris software can be manipulated to send different host headers and separately keep logs for each of the hosts if its target is a virtual host.
The software is capable of not creating a log file during an attack, which makes it possible to catch unmonitored web servers off-guard and slip past without triggering red flags in the entries of the log file.




