In computer use, a zombie is a computer connected to a network that has been compromised by a virus, virus, or Trojan. It can be used remotely for malicious activities.
Most owners of zombie computers do not realize that their system is used in this way, which is why they are compared to the living dead. They are also used in DDoS attacks by linking bottles similar to the usual zombie attack of horror films.
What are they used for?
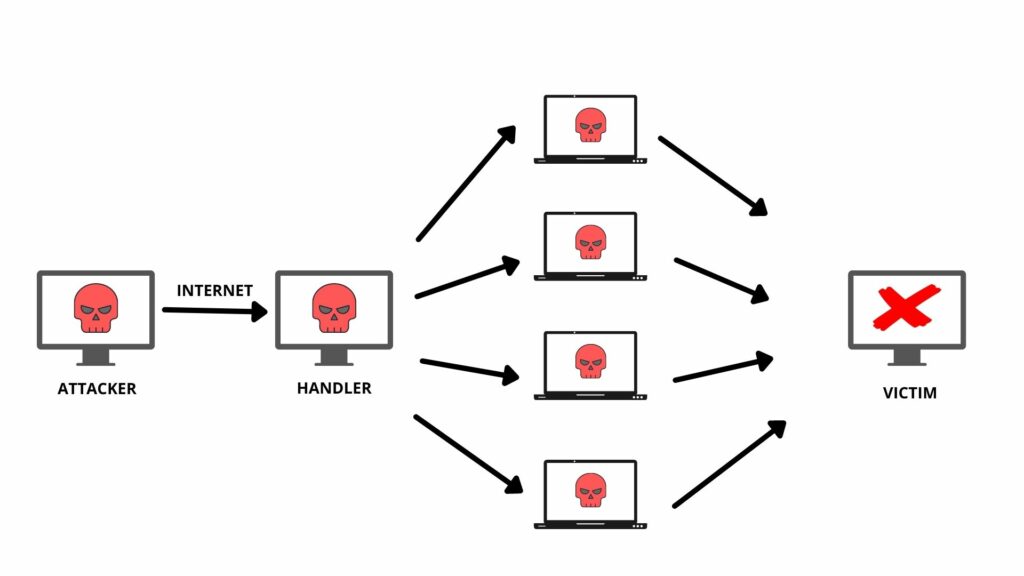
Zombies are frequently used in denial-of-service (DDoS) attacks, which means the proliferation of websites with multiple computers simultaneously. With multiple users simultaneously making requests to a server hosting a Web page, the server crashes, denying access to real users.
The variation of this type of landfill is known as an offensive service attack. It uses ’emulsive Zombies’: downtime by filling websites at low times to slow down, rather than block, targeted websites. Such attacks are difficult to detect because slow service may be unavailable for months or even years or is simply thought to be due to other problems.
Zombies are also used to send spam. In 2005, it was estimated that between 50% and 80% of all broadcasters were sent by zombie computers. This method is helpful for criminals as it helps them avoid detection and, at the same time, reduces bandwidth costs (as Zombie owners will incur fees).
This type of spam is also used to spread Trojans, as this type of malware is not automatic but relies on email transmission to spread, unlike worms that spread in other ways. For the same reasons, Zombies are used to scamming sites with ads that are based on each click, which increases the number of hits incorrectly.
Major attacks
In 2000, many high-profile websites (such as Yahoo or eBay) crashed into a work-sharing attack by a young Canadian man using the nickname MafiaBoy. Later, other significant attacks and service threats were used in the same model, such as those aimed at anti-spam programs, such as SPEWS in 2003 or those targeted at Blue Frog in 2006.
Most recently, in 2010, a criminal network called Mariposa, which controlled some 13 million computers, was brought down to Spain by the Spanish Civil Guard Telematic Crime Brigade and arrested. They had data from 800,000 people in 180 countries.
How to protect yourself
Mindfulness and alertness are the best security tools to prevent these types of attacks. Sound advice includes not visiting suspicious websites, not downloading suspicious files, and not clicking on suspicious messages.
It is also important to avoid useless websites or anonymous companies, download only from trusted sources, and use security measures on your computer, such as antivirus, antispam, or firewall solutions.